Expert-driven, modern pentesting
Drive effective security outcomes with Pentest as a Service (PTaaS), tailored for organizations demanding quality and speed.
HackerOne Agentic PTaaS
Agentic PTaaS is built on the proven foundation of HackerOne PTaaS and takes a fundamentally different approach from both traditional services and fully autonomous tools. A coordinated system of AI agents and human experts scales reconnaissance, setup, exploitation, and validation across large and changing attack surfaces while preserving judgment, accountability, and trust.
The outcome is faster, evidence-backed answers to what matters now.
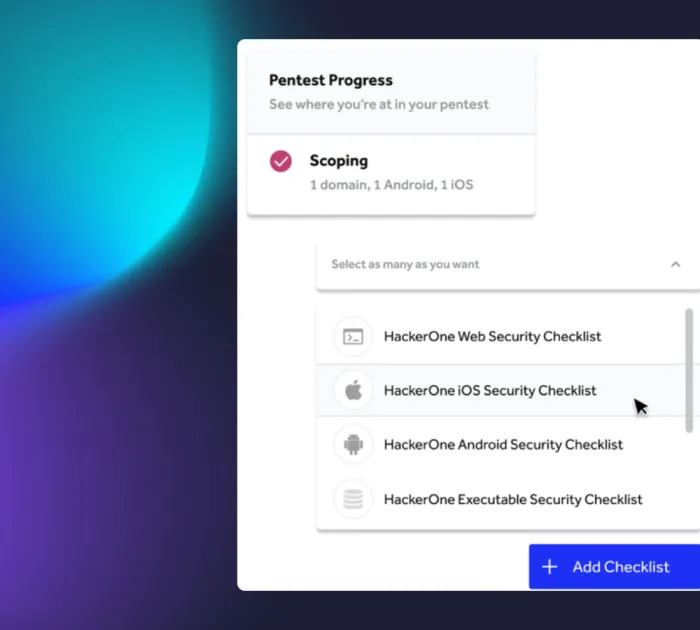
Scoping
The pentesting process begins by defining the test's scope, whether it's web apps, APIs, internal/external networks, or cloud environments. HackerOne’s Pentest Scoping Assistant acts as a guided teammate during kickoff, helping you capture the technical, business, and risk context needed for high-quality testing.
- Custom-tailor the pentest to specific systems, applications, or networks.
- Pentesters map out potential vulnerabilities through reconnaissance and prioritize based on risk.
Agentic + Human-led testing
Each pentest engagement is tailored to your assets, technologies, and risk profile, delivering high-confidence findings you can act on immediately.
- Elite pentesters are carefully matched to your asset type and technology stack for precise, high-impact testing.
- Testing aligns with industry standards while adapting to how real attackers operate in modern environments.
- Every vulnerability is reviewed, validated, and documented by expert pentesters.
- Findings are delivered live through the HackerOne platform, enabling faster remediation and tighter collaboration with engineering teams.
Agentic support: For supported web application tests, agentic systems may assist with reconnaissance and repeatable validation under strict guardrails. Human pentesters retain full oversight and review all agent findings for quality, accuracy, and relevance.
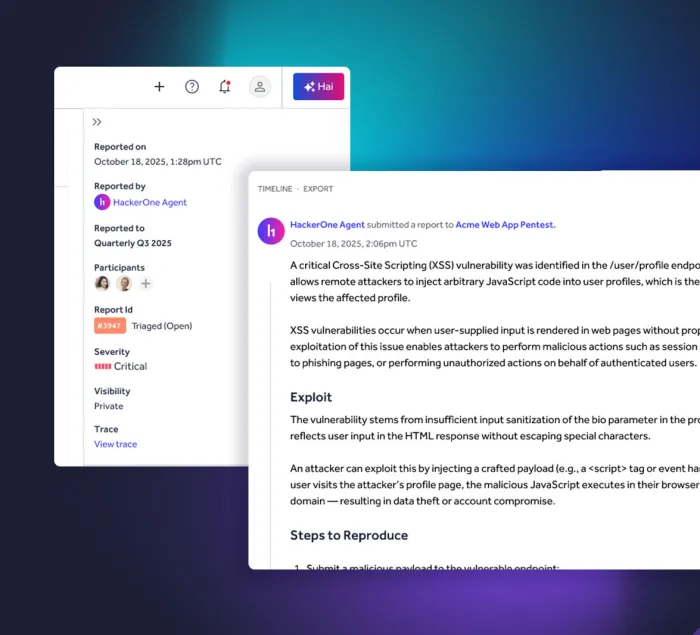
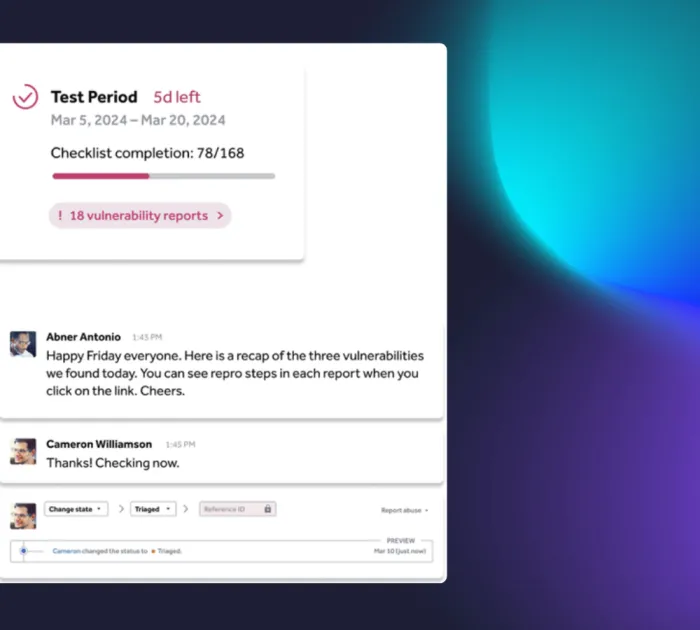
Real-time reporting and collaboration
Get real-time insights into vulnerabilities as they are discovered. In the PTaaS dashboard, customers can track findings, collaborate with pentesters, and begin remediation while the test is still in progress.
- Engage with pentesters via integrated tools like GitHub, Jira, Slack, and ServiceNow.
- Gain immediate visibility into critical vulnerabilities for faster decision-making and remediation.
- Coordinate with the security team in real time, ensuring fast fixes.
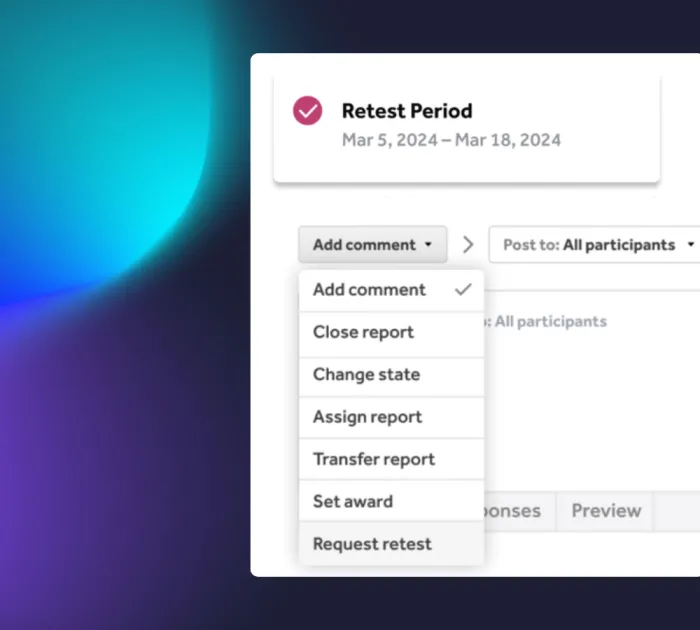
Validation of fixes + retesting
After vulnerabilities are identified and remediated, HackerOne provides retesting to confirm that the fixes have been correctly implemented so no gaps remain in your security posture.
- Once fixes are applied, retesting ensures vulnerabilities are fully resolved.
- Testers revisit the vulnerabilities and validate that all patches are successful.
- Monitor the status of vulnerability fixes directly through the platform.
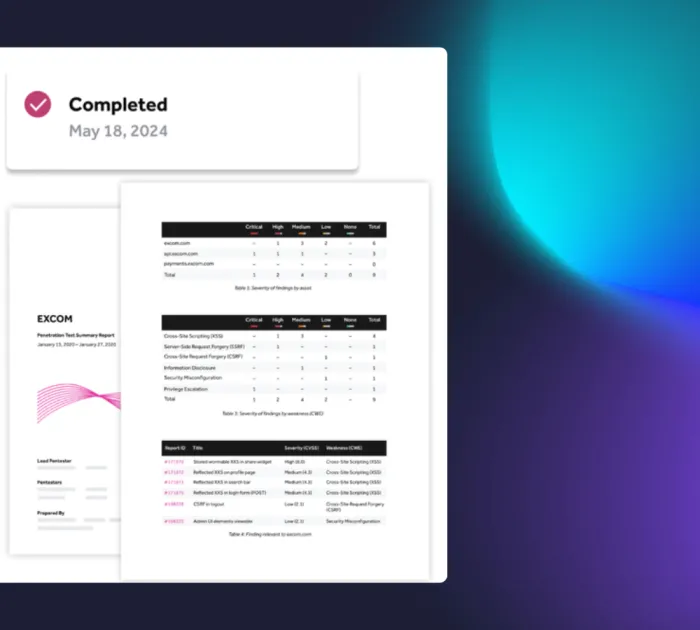
Final pentest report
At the conclusion of every pentest, you receive a comprehensive report that includes all findings, risk assessments, and remediation guidance.
- Receive detailed reports with vulnerability analysis, including proofs of concept and recommendations for fixes.
- Meet standards for SOC 2, ISO 27001, GDPR, and more with a report that proves security due diligence.
- Access easy-to-understand recommendations and clear next steps for addressing security weaknesses.
Compliance
Click on the security standard logos to learn how HackerOne addresses compliance for each.
Hai: Your HackerOne GenAI copilot
Our in-platform AI copilot provides an immediate understanding of your security program so you can make decisions and deliver fixes faster. Effortlessly translate natural language into queries, enrich reports with context, and use platform data to generate recommendations.
Security advisory services
Manage and scale your pentesting program with best practices and insights from experts in cyber risk reduction. Our solutions architects help tailor your program—from custom workflows to KPIs for measuring program success.