One Platform for Continuous Exposure Reduction
Agentic AI + human intelligence working together to discover, validate, and eliminate real-world threats across your entire attack surface.
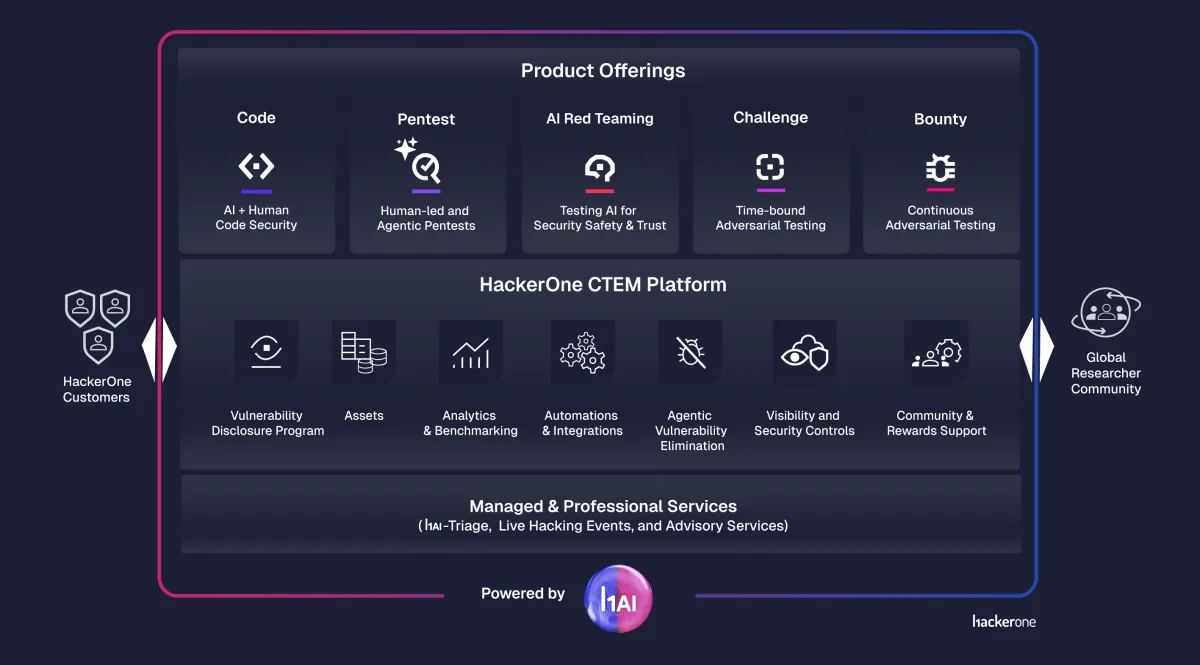
Transform security decisions with coordinated AI agents
Hai, HackerOne’s agentic AI system, works across every stage of CTEM—analyzing findings, enriching context, identifying patterns, and accelerating validation and prioritization. With coordinated agents powering every workflow, security teams get clearer signals, faster decisions, and continuous exposure reduction.
Analytics powered by real-world exposure data
Leverage insights from more than 500,000 validated, real-world findings. Track exposure trends, measure program effectiveness, and make data-driven decisions that keep pace with evolving threats and attacker behavior.
Human expertise at global scale
Tap into a curated global network of security researchers who continuously uncover and validate real-world exposures. With verification, mediation, and payments managed by the HackerOne Platform, your teams stay focused on rapid remediation and risk reduction.
Centralized exposure management
Maintain visibility across your expanding attack surface with a unified asset inventory. Map assets to exposures, apply risk-based context, and feed everything into continuous discovery, validation, and remediation workflows, so no critical risk goes unnoticed or unaddressed.
Streamlined workflows and integrations
Connect HackerOne to your development and security ecosystem to automate ownership, routing, and remediation. With 30+ integrations, exposures move seamlessly from discovery to validation to fix—reducing manual work and accelerating time to remediation.
One platform, dual force: Human minds + AI power
Combining human insights and AI-powered solutions for unmatched vulnerability elimination
across the software development lifecycle.

Maximize your ROI
Get the most from your investment in HackerOne with expert services that help you prioritize reports, accelerate remediation, and implement best practices.