Stop attackers in their tracks with targeted, offensive testing.
Use insights from the world’s top security researchers to hunt down and remediate the most elusive vulnerabilities—quickly, effectively, and on your terms.
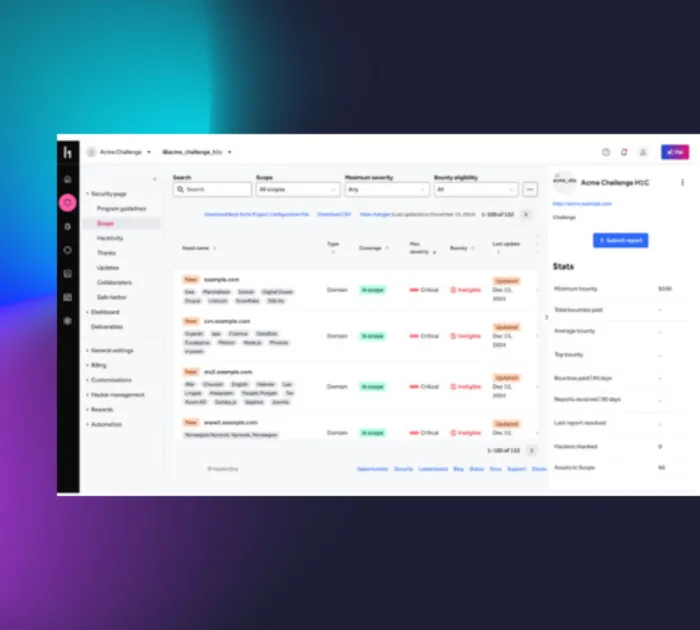
Scoping and setup
Begin by defining the engagement’s scope including assets, duration, and specific objectives - with the assistance of a HackerOne technical engagement manager.
- Target specific assets like web applications, APIs, or newly released features to meet critical security objectives.
- Set engagement parameters, including duration (15-, 30-, 60-day challenges), and invite researchers with the required expertise.
- Begin testing in as little as two weeks with streamlined processes.
Customized offensive testing
Engage a curated group of security researchers to conduct time-bound, offensive testing to uncover exploitable vulnerabilities.
- Invite ID-verified and background-checked security researchers based on your specific requirements.
- Use offensive testing strategies to uncover vulnerabilities not detectable by automation or other testing methods.
- Focus on high-value initiatives like validating new security controls or identifying critical flaws in production systems.
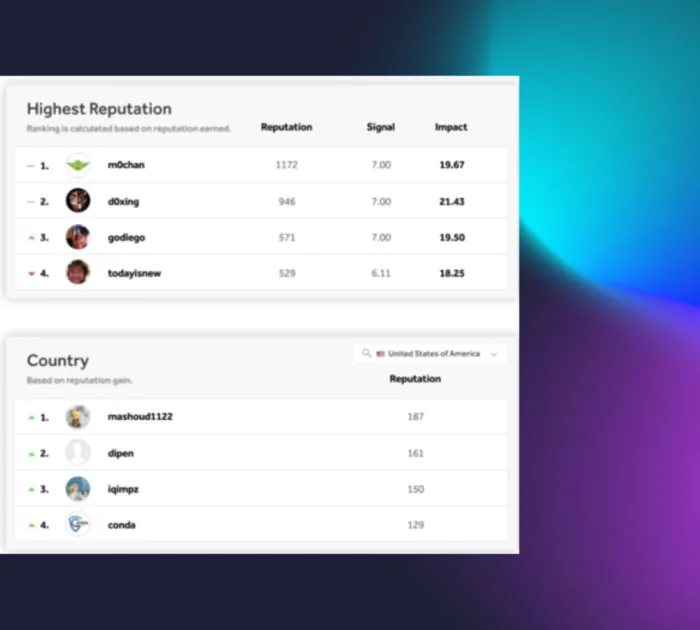
Collaboration and insights
Gain actionable insights throughout the engagement via the HackerOne Platform.
- Track vulnerabilities as they’re discovered and start remediation immediately.
- Integrate findings with your DevSecOps workflows using tools like Jira and GitHub for streamlined collaboration.
- Engage directly with researchers and your internal team to resolve issues efficiently.
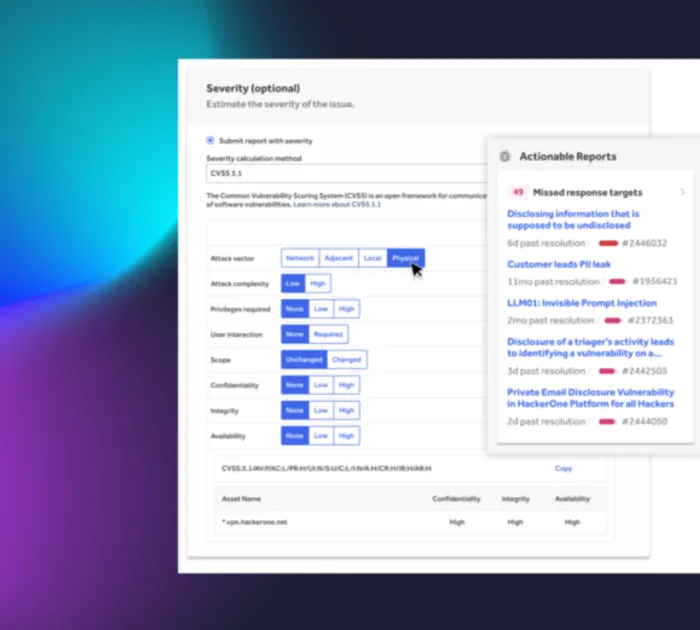
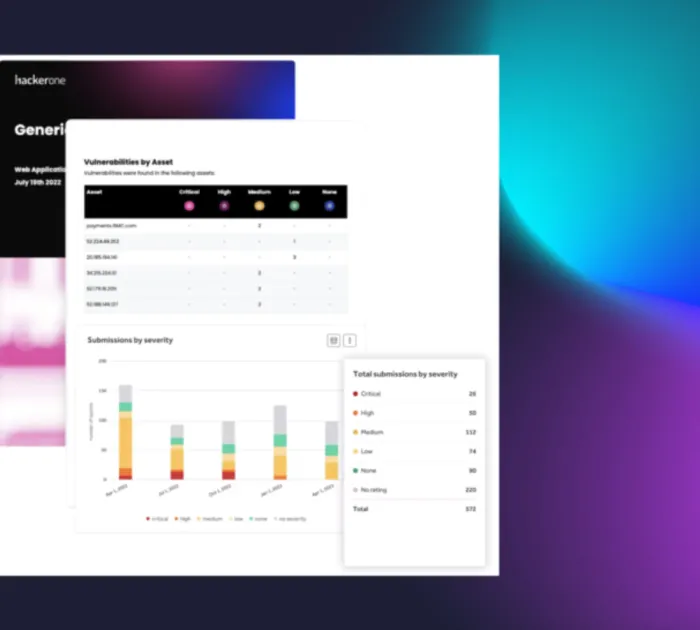
Reporting and remediation
Receive a detailed report at the end of the challenge, including all findings, risk assessments, and remediation recommendations.
- All vulnerability findings are reported within the HackerOne Platform, as well as in a consumable PDF for compliance needs.
- Feed vulnerability data into your existing bug-tracking tools, including JIRA and GitHub.
- Go even deeper with a Spot Check focusing precisely on areas of concern, whether it’s a particular feature, endpoint, vulnerability, or asset.