What to Look For in a Penetration Testing Company

What are Penetration Tests?
Penetration testing is one of the most widely used techniques for complying with security regulations and protecting networks, computing systems, and users.
In a penetration test, or pentest for short, authorized hackers simulate an attack on specific applications, networks, or sites to assess their security. A penetration test is designed with a specific goal in mind, such as to gain privileged access to a sensitive system or to steal data from a system that is believed to be secure.
Traditional vs Hacker-Powered Pentests
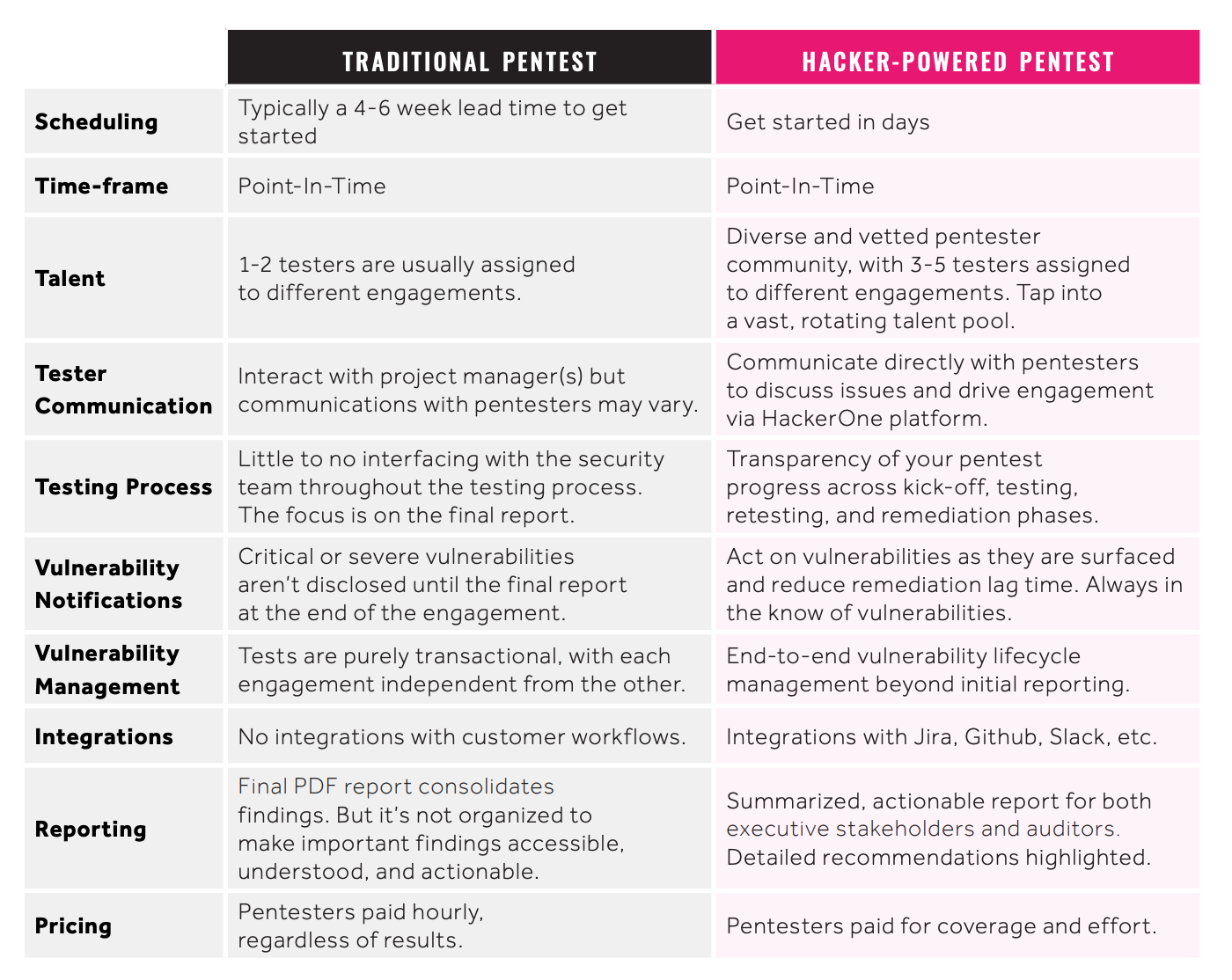
In traditional penetration tests, one or a small number of researchers run tests and produce a report for a fee. Traditional penetration test reports are often expensive and many experts predict they're on their way out. Importantly, they cost the same regardless of the quantity or severity of the vulnerabilities they surface.
Hacker-powered penetration tests are emerging as a more cost-effective way to harden application security. With HackerOne Pentest, selected hackers from our community are invited to find vulnerabilities in your systems, and you are able to tap into a vast, rotating talent pool.
 5 key things to look for in a penetration testing company
5 key things to look for in a penetration testing company
1. Visibility into the Testing Process
In traditional penetration testing, customers often lack visibility into the pentest engagement. Critical vulnerabilities aren’t communicated to internal stakeholders in a streamlined way, and remediation workflows often aren’t baked into the expected delivery. Customers should look for a transparent vendor so they know what’s happening across the entire testing window.
With HackerOne, companies can act on vulnerabilities as they are surfaced, gaining visibility into the pentest progress across kick-off, retesting, and remediation phases. Having a transparent view into the testing process and being able to act on reports immediately helps shorten time to remediation, cutting overall costs.
2. Integrations into your SDLC
More often than not, the cost and effort of a pentest is focused on the final PDF delivery. Though critical, the report is usually excessively long and does nothing to clarify remediation priorities. Pentest platforms should seamlessly integrate with all aspects of the software development lifecycle (SDLC) so findings are pushed to the right developer and vulnerabilities are fixed faster.
With HackerOne, gain unparalleled access and control through integrations with Jira, Github, Slack and more.
3. Diverse and Collaborative Pentesters
Traditional security research firms will typically deploy one to three researchers for a penetration test, and often they are entry-level practitioners. Generally there’s little to no customer interaction with pentesters.
At HackerOne, we find value from working in a collaborative environment that cultivates discussion. Every pentest at HackerOne has a team of 3-5 testers assigned to the engagement. Customers can communicate directly with pentesters to discuss issues via HackerOne’s platform. With a community of diverse skill sets and experiences, work with different background checked and vetted pentesters across engagements depending on scope needs.
4. Speed of Delivery
An important factor to consider is pentest completion timeliness. Depending on the number of tests you’re aiming to run, know your timelines and how quickly you need to get things done. Speed of delivery can vary across vendors. Some vendors require a 4-6 week queue time, some charge extra to expedite timelines, and some can get started in anywhere from 24 hours to a few days.
At HackerOne, we tap into the vast community of hackers to get started in as little as seven days, depending on testing environment readiness.
5. Long-term Security Goals
Customers should consider what their security goals are as they go through security-specific vendor evaluations. How often do you need to run pentests? What compliance initiatives are you looking to satisfy? Are you looking for a more holistic and longer term pentesting strategy? There are unique advantages across different security vendors, who may specialize in point-in-time testing vs continuous testing capabilities.
At HackerOne, we encourage customers to not only use pentest for compliance needs, but to incorporate pentesting as part of a longer term security strategy. Customers can easily add a HackerOne Bounty or complement an existing bounty program to think about an end-to-end vulnerability lifecycle management beyond point in time tests.
To start a HackerOne Pentest today, or learn more, contact us


