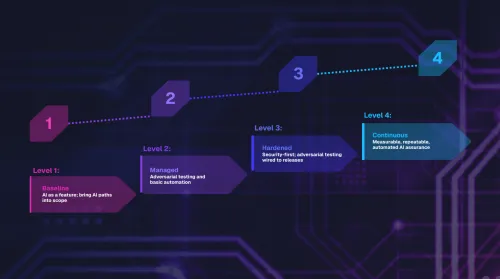
Choose the right AI testing method based on your risk maturity, from add-on LLM pentests to continuous AI assurance. Understand what each level provides.
HackerOne Blog
The latest from HackerOne
Image

Traditional pentests can’t keep pace with modern development. Agentic Pentest as a Service delivers continuous, human-validated security at scale.