Where security researchers learn and earn
- Build your skills with educational materials for all levels
- Put your skills to work with hundreds of bug bounty programs and hacking engagements
The community by the numbers
Benefits for the HackerOne Community
Exclusive discounts and opportunities for HackerOne hackers through our amazing partner network.

Let the world know you're a hacker
Hacking is a calling, a career, a constant journey of challenging yourself and pushing the limits of technology for the betterment of society.
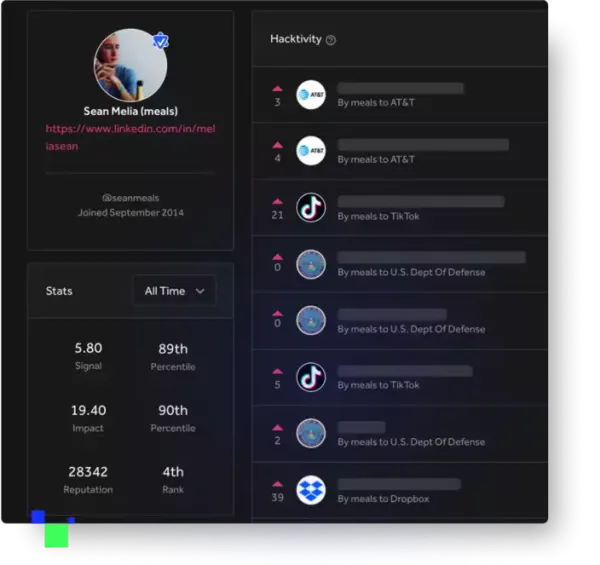
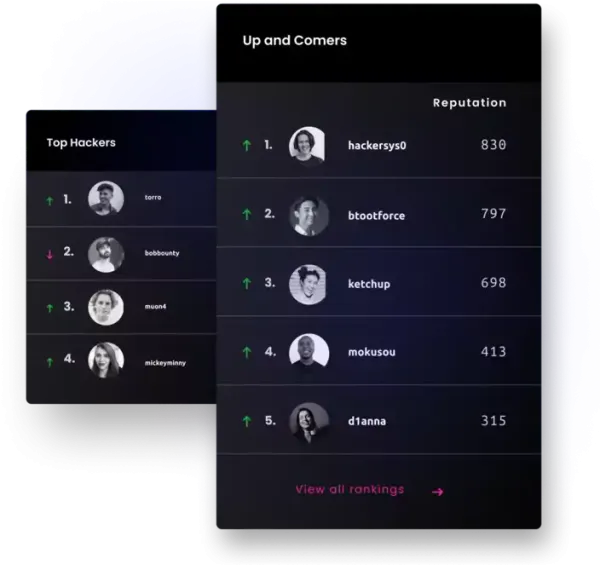
From earning reputation, signal, and impact scores, to competing for the most critical bugs submitted in a quarter, to testing your skills in the Hacker101 CTF, there's a challenge waiting for you.
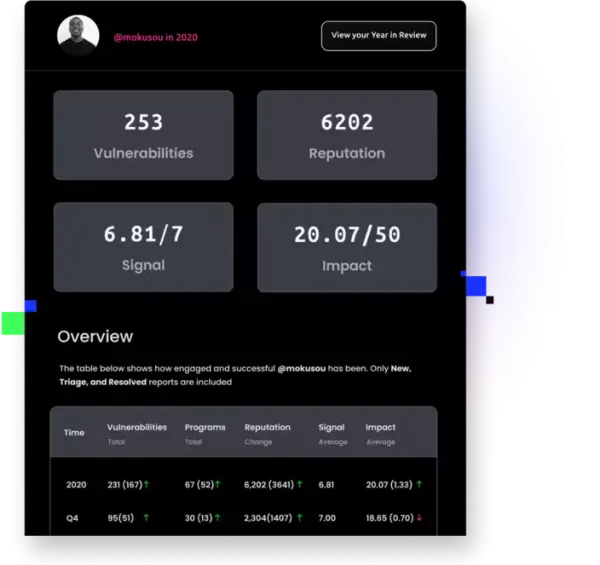
Get your full yearly stats in a beautifully designed pdf that can be shared across your social media and with prospective employers
Sign-up for an account. You will need a name, username, and a valid email address. You can remain anonymous with a pseudonym, but if you are awarded a bounty you will need to provide your identity to HackerOne. Be sure to take a look at our Disclosure Guidelines which outline the basic expectations that both security teams and hackers agree to when joining HackerOne.
Find a participating program. Read the Security Page closely, which will give you the information you need to participate in the program, including the scope of the program and reward expectations. Programs can offer thanks, swag, and/or bounties for valid reports; every program is different and it’s at the discretion of the program what sort of reward they offer, so be sure to check that out before you submit a report. Start hacking and submitting reports. Your reports should include a detailed description of your discovery with clear, concise reproducible steps or a working proof-of-concept (POC). If you don't explain the vulnerability in detail, there may be significant delays in the disclosure process, which is undesirable for everyone. If you’re not sure what a good report looks like, here are some tips.
Congrats on finding a security vulnerability, that’s exciting! You can use the HackerOne Directory to find the appropriate method to contact the organization. Some companies prefer you reach out to them through HackerOne, some through email. All the information is on their profile. Just search for their company name and their preferred method will come up.
Here’s an example of a company who handles reports on HackerOne: https://hackerone.com/twitter
Here’s an example of an organization that prefers email: https://hackerone.com/ncsc
Picking a program to hack on is easy! Go to the HackerOne programs overview and pick an exciting-looking program. The overview will list all the public HackerOne programs and the ones you’re invited to. Then read the program policy and scope to make sure you don’t hack anything you’re not supposed to
Before you submit a security vulnerability, make sure to read through the program’s scope. The scope determines whether or not a company is interested in a particular vulnerability. Once you have confirmed the program will accept the vulnerability, be sure to submit the issue to the program.
A good report is made up of a few things — a descriptive title, a thorough explanation and proof of concept, and metadata. @nahamsec wrote a great guide on how to write a good report. You can read it here: https://docs.hackerone.com/programs/quality-reports.html.
As we recently surpassed $100 million dollars in bounties, we want to continue the celebration with this list of 100 tools and resources for hackers! These range from beginner to expert. Most are free but some cost money. Read all about them here.
A company will review the contents and triage the vulnerability. You can review the Response Efficiency metrics on a company’s policy page. This will help you determine how quickly a company responds, bounties and resolves the bug.
The hacker community is a group of tens of thousands of people that make the internet safer for everyone. A lot of us are learning new things every day. In order for us to excel and discover new techniques and entire vulnerability classes, we try to share as much information as possible. This is often done through blog posts, how tos, CTF challenges, public disclosure, or a simple tweet. This is one of the things that makes this such an amazing community!
Hacktivity is the front page of our community showcasing select activity regarding vulnerabilities (once disclosed), hackers, programs, and bounty awards. In this article, we'll answer the most frequently asked questions regarding Hacktivity.

