What To Do When You're Stuck Hacking

Hacking can be tedious work. Sometimes you’ve been looking for hours, perhaps days, and you’re unable to find a security vulnerability. It can be demotivating at times. This blog will give you multiple tips to power through it and regain that sweet, sweet feeling of submitting a security vulnerability.
This feeling isn't great
Something that I’ve seen is important, is knowing what you’re looking for. A lot of hackers often just “go look for something”. The lack of focus here, especially with new hackers, doesn’t help you find vulnerabilities. It often results in moving on too quickly, not knowing what to look for exactly, or the feeling that you’ve looked at everything already. So, whenever you’re stuck, ask yourself this question first:
“What am I looking for?”
Make sure you have a clear goal. For example, the answer the this question should never be “I am looking for a security vulnerability.” Instead, it could be “For the next two hours, I am looking for an Insecure Direct Object Reference (IDOR) vulnerability.” This has multiple benefits:
- You’re setting a hard deadline for yourself
- You know what to test for
- You know which resources to look for to learn more about the vulnerability
- You can ask very specific questions to peers
- You discover new attack surface each time you change your goal for the same asset
- You’ll be able to prioritize what to look at based on what you’re looking for
When you come across something interesting during hacking, make a note of it and come back to it later if it doesn’t help you reach your goal. Whenever you set a goal, make sure it is SMART.
Take your mind off of it
There are different kinds of “being stuck.” There will be times where you’re trying to exploit something and there just doesn’t seem to be a way. People have different things that gets their mind off of hacking, but here’s a list of five things you can try (thanks everyone that helped put this list together!):
- Workout / go outside
- Grab some food
- Play a (video) game
- Nap / sleep
- Make music
Explore and learn
As a hacker it is important to know what you know, but it is even more important to know what you don’t know. Hackers are always learning. Bug bounty programs and vulnerability disclosure programs are often a black box, which is why you need some structure to get through it. Black boxes often make you feel that there’s nothing left to look at when you try to do multiple things at the same time. When you structure your work, you’ll be able to plan what you want to explore and learn. When you’ve never found an XML External Entity (XXE) vulnerability, like myself, you could set that as your goal. This will help you:
- figure out what you need to know before you can go look for it in the wild
- search the HackerOne Hacktivity to read about other people their XXE vulnerabilities
- learn about it and exploit it on Hacker101
- pinpoint a feature or asset you’ve looked at in the past that you could target
An interesting exercise that I like to do, is to try to “guess” how the backend is implemented by implementing it myself. Simply write the code that mimics the behavior that you see. This has helped me multiple times to figure out an exploit. In the case it didn’t help me exploit something, it helped me gain insight into the defenses.
Make notes and reminders
I make a lot of notes when I’m hacking. Behavior that I think is interesting, newly discovered attack surface, vulnerabilities I’m stuck on, and low severity vulnerabilities that aren’t worth reporting by themselves (but can perhaps be leveraged in a chain!). When I’m stuck I often find myself going through these notes to help me come up with another strategy to attack something. I have simple sections and keywords in these notes to quickly go through them:
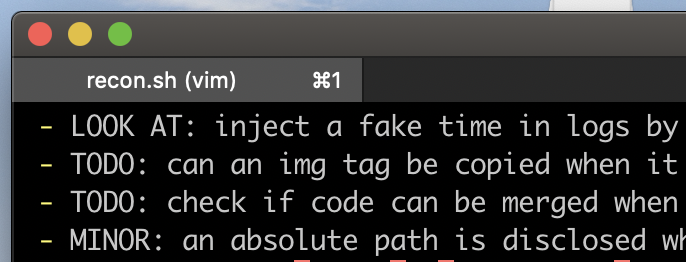
Taking notes with recon.sh
“I’m new to BBP and I don’t feel confident that I can find something in public programs”
You’re not alone. This is something a lot of hackers struggle with. If you haven’t found a lot of security vulnerabilities yet, it might pay off to start with Capture The Flags (CTFs) instead. Exploiting something for the first time is hard and eye-opening — let alone doing this in production environments. My suggestion would be to apply the same structure you would apply when looking in real targets, this will help you build a solid foundation and will help you become an amazing hacker.
Keep going!
At the end of the day, being stuck is just another part of becoming a hacker. I’d encourage you to figure out what helps you to eventually solve the problem or being OK with moving on to another problem. All hackers have been stuck and will continue to be so occasionally.
Happy hacking!
Jobert
HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited. As the contemporary alternative to traditional penetration testing, our bug bounty
program solutions encompass vulnerability assessment, crowdsourced testing and responsible disclosure management. Discover more about our security testing solutions or Contact Us today.


