Your First 90 Days as Security Lead, Part 1: Building Your Security Foundation

Congratulations! You’ve just been named the new security lead for your organization. You probably have many projects swirling through your mind, like addressing a critical issue, benchmarking your organization against peers, or developing a broad plan.
We interviewed a variety of security experts—some who’ve run security programs in the past and others who now help HackerOne customers develop and scale their programs—to get their advice on how new security leads should spend their first three months. At HackerOne, we’ve worked with many firms as they’ve launched, expanded, and formalized their internal security team and functions, and we included those experiences as well. The consensus first step: it's critical to understand why you're there and how you're going to set the foundation for your security program.
This two-part blog series details best practices for developing your program and the key steps to take during the first three months in your new role. So let’s dive in!
Understand what prompted your role
Typically, there are a few common triggers for creating or expanding security within an organization but it boils down to risk reduction. Here are the common mechanisms driving the need for a security lead:
C-Level Decree: As organizations grow their approach to security can become more muddied and murky. Add in the increasingly mainstream exposure (and accompanying negative brand and financial fallout) of security incidents and you’ll see wary executives call for more accountability. They’ll typically want to understand the cyber risks and readiness, especially versus relevant benchmarks, and may ask questions about “reasonable care” in securing corporate data.
Scalability: Expansions to different regions may subject organizations to new laws and regulations, like GDPR and NYDFS, while acquisitions and new product launches may uncover mismatched or incomplete security processes. As an organization’s security footprint increases, the need for a formal team and leader becomes more apparent.
Proactive vs. Reactive: As more hackers find and report more potential vulnerabilities, organizations are being made painfully aware of limitations in security processes and accountability. Appointing a security lead gives organizations more proactive control over how security is handled, how processes are implemented, and even how engineering, legal, and other teams build security into their own processes.
Whatever the trigger, your job is to now understand your current security posture, identify and prioritize focus areas, and get to work. But not necessarily in that order.
The shifting cybersecurity paradigm
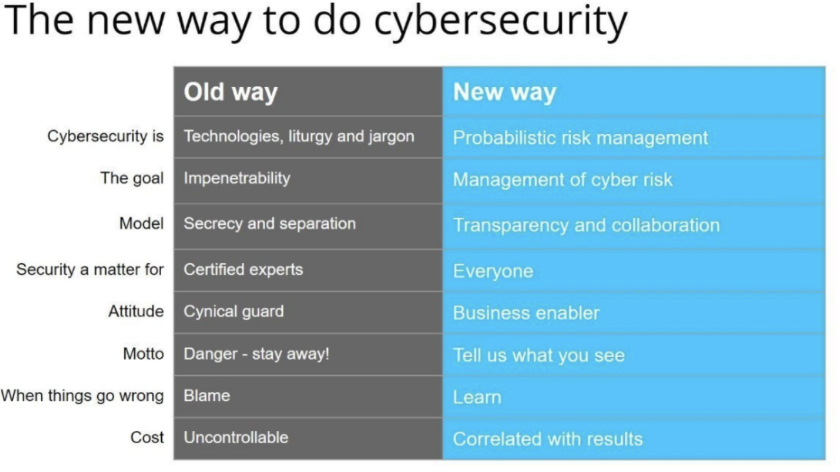
Understanding the changing approach to security is also important, especially as you get started. There has been a dramatic shift away from the traditional cybersecurity “fortress” strategy to a new, modern approach that understands there is no way to be 100% secure.
Building a fortress has been the typical security model for years, where firewalls are expected to protect assets from outsiders and a limited number of entry points enable the tracking of data flow and access. Once inside, however, users have free access (because, presumably, they've been vetted). It essentially relies upon one hardened entry point that, if overcome, leaves everything of value unprotected.
This is no longer safe because criminals have figured out how to get over these walls with social engineering, malware, and other tactics. Plus, humans tend to make mistakes and leave a known or unknown door open by placing data on a public server or failing to patch a technology gap.
Today, it’s clear this fortress approach has become insufficient on almost every front.
Arriving at the airport model

The new approach to cybersecurity is analogous to how an airport approaches security, with many layers of vetting, many different types of security, and many different areas requiring different credentials to access.
In an airport, anyone can walk into the ticketing area. But to get past the first security point, your documents are closely checked, then you and your bags pass through machines that scan for liquids, flammables, and weapons. Then, getting on the airplane requires a barcode scan of your boarding pass, getting on the tarmac requires a badge and a door access code, and so on. This multi-layered approach to security uses varying safeguards as travelers and workers move between areas requiring more or different security.
For cybersecurity, that’s akin to multiple levels of firewalls and passwords, two-factor authentication, biometrics, logging and surveillance to alert to odd activity, additional focus on critical assets, and more. This strategy, termed “defense in depth”, relies on continuous and ever-more stringent access and technological controls.
Focus on managing probabilistic risk, not eliminating it
There is no way to achieve complete security. With the world becoming more connected and data becoming more centralized, the need for access will only increase. That means, in your new role, you’re charged with focusing your limited resources based on the highest risk.
First, however, you’ll need to understand which risks are greatest and which of those are most likely. Probabilistic risk management or assessment is the process of identifying a specific problem, gauging the possible damage from it, and estimating the likelihood of it happening. From there, you can prioritize where to focus your efforts.
Your goal now is to manage risk as best as possible, to be transparent on vulnerabilities and collaborate with others on solutions and tactics, and to be open (and thankful) to anyone who points out a potential security gap. Today, organizations are more open to learn from every security experience, to share with others, and to correlate actions with results.
This openness is reflected in the huge number of industry groups and government agencies promoting vulnerability disclosure policies as a best practice. It’s also apparent in the increasing prevalence of legislation and regulation covering data privacy, access, and disclosure.
So how does a new security lead embrace this new cybersecurity model? Check out “Part 2: Build a Plan and Get to Work” to find out.
HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited. As the contemporary alternative to traditional penetration testing, our bug bounty program solutions encompass vulnerability assessment, crowdsourced testing and responsible disclosure management. Discover more about our security testing solutions or Contact Us today.


