Integrate HackerOne directly into your website with Embedded Submissions

Receiving vulnerabilities has never been easier with the release of our newest integration: Embedded Submissions. What started with Email forwarding in 2017, is now being taken to the next level. With this integration, we’re taking away any friction that might occur when letting finders send an email, or pointing them to a different website to report their vulnerability. The HackerOne submission form will be embedded directly on your website by simply adding one line of JavaScript on your web page.
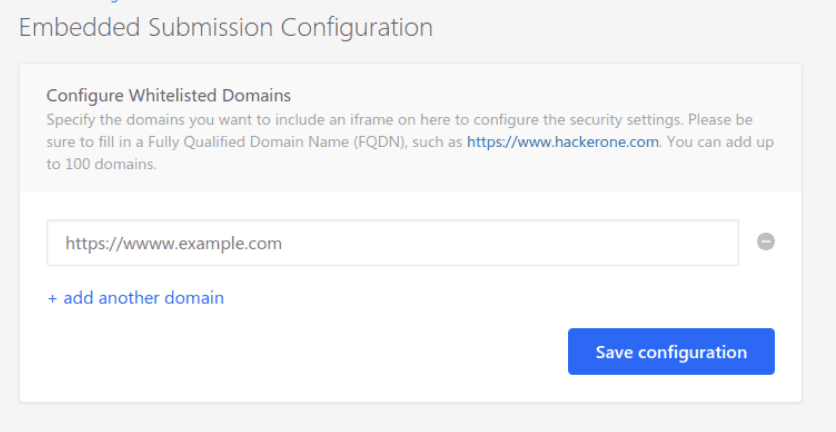
The Embedded submissions feature enable organizations to embed the HackerOne vulnerability form onto their own website. Reports can be submitted directly through the organization's website rather than navigating to HackerOne. Furthermore, this allows hackers who do not have a HackerOne account to submit vulnerabilities.
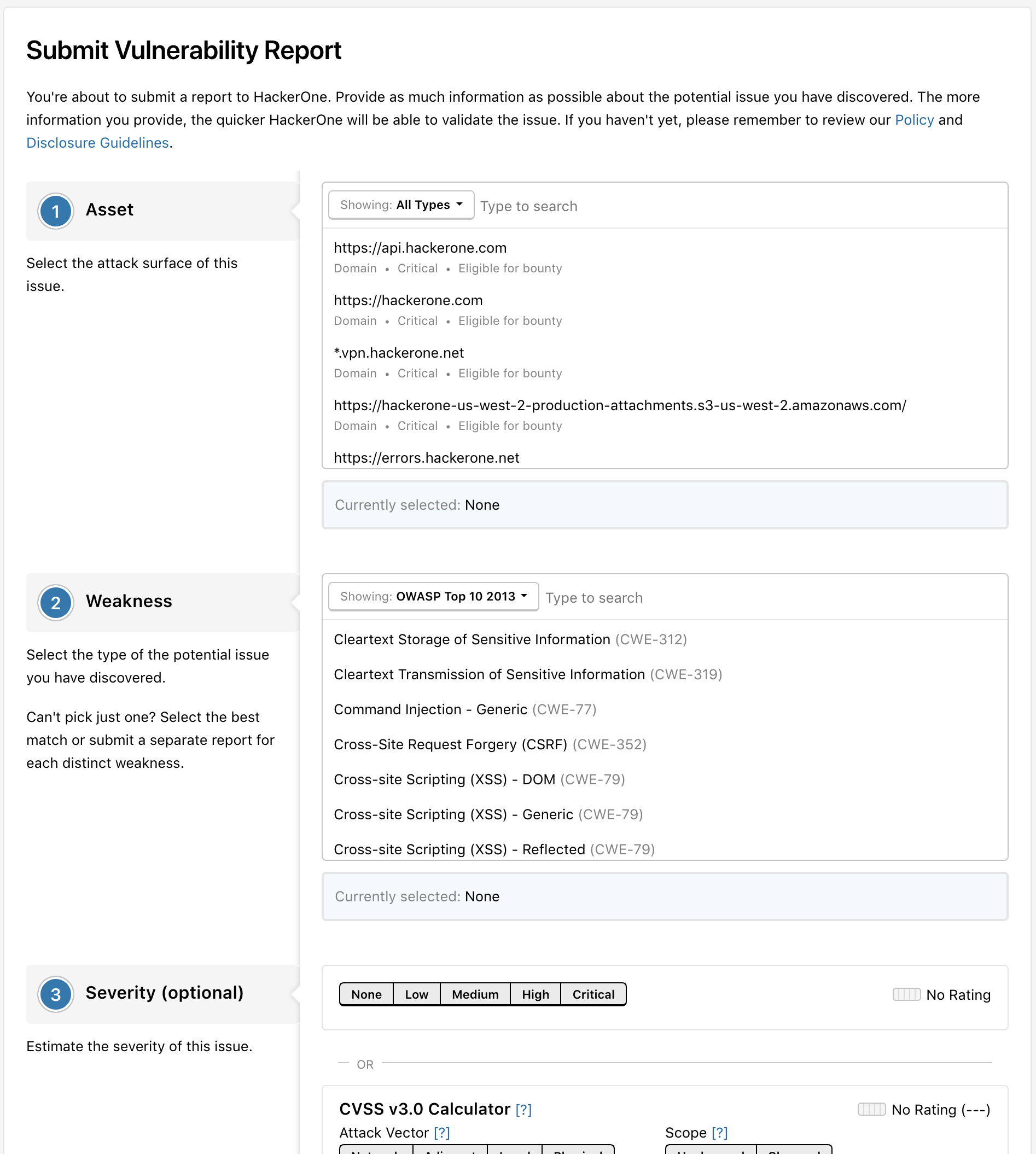
Users that want to stay anonymous, can stay anonymous
With the introduction of this integration, we’re adding the option for finders to submit anonymously. This allows good Samaritans to elect anonymity if they desire it, removing another barrier that can prevent someone from notifying you of a security vulnerability. HackerOne’s Embedded Submission form is the first of its kind that allows anonymous submissions.
Of course, anonymously submitted vulnerabilities will be validated and triaged using noise filters (Human Augmented Signal) as per the normal triage process. If a hacker later decides to create a HackerOne account, they can claim the reputation for their valid submission.
Get started
Embedded Submissions is available starting today for all customers. Check out our documentation for more information and let us know if you have any feedback or questions. We would love to hear your feedback.
HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited. As the contemporary alternative to traditional penetration testing, our bug bounty program solutions encompass vulnerability assessment, crowdsourced testing and responsible disclosure management. Discover more about our security testing solutions or Contact Us today.



