5 Hacker-Powered Trends You Need to Know About

The Hacker-Powered Security Report examines the largest dataset of more than 800 hacker-powered security programs, compiles learnings from application security practitioners and the hackers who participate in bug bounty and vulnerability disclosure programs.
For your quick reference, we’ve distilled the report to 5 key trends that show how white-hat hackers are shaping the world of security.
Growth in Bug Bounties
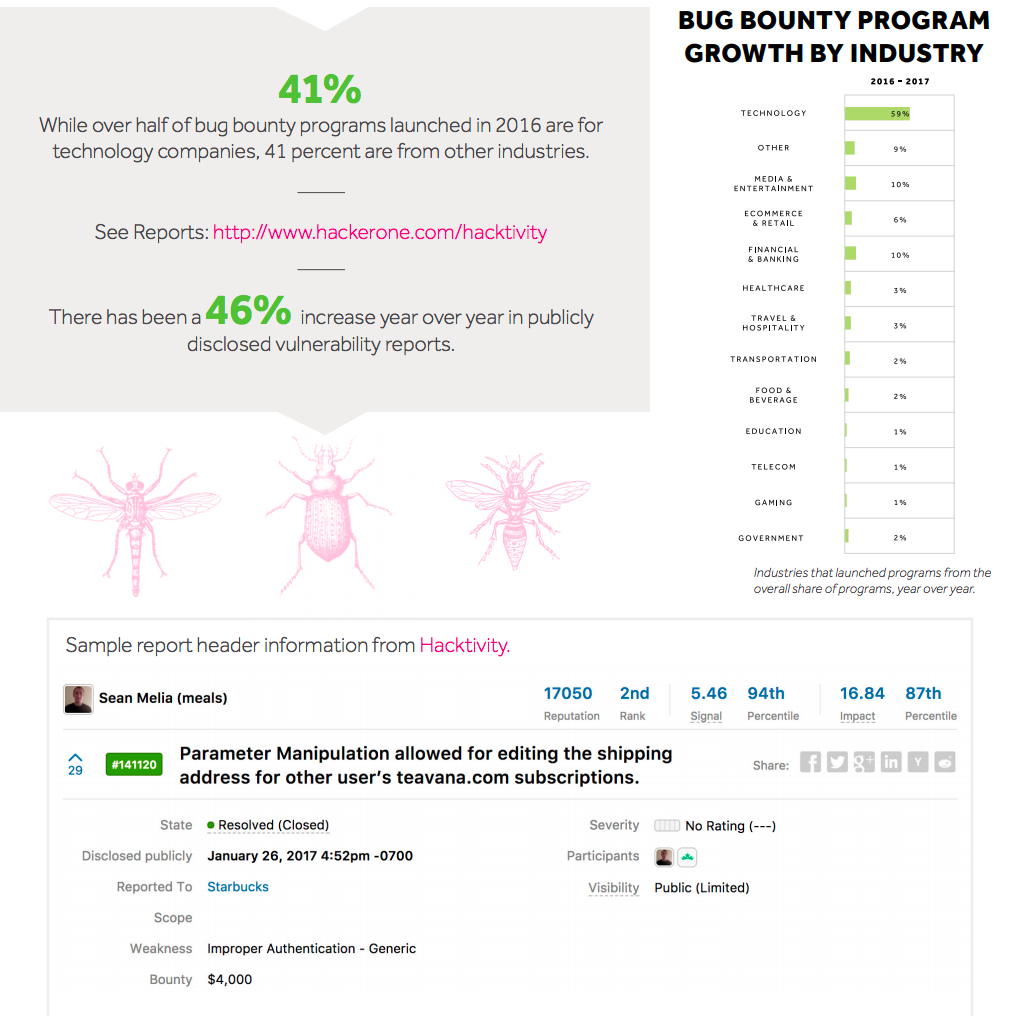
Forty-one percent of new bug bounty programs launched between January 2016 to 2017 came from industries beyond technology. Within technology there was an increase in the number of Internet of Things (IoT) and smart home programs launched, as well as open-source projects. While technology companies still represent the majority (59%), growing verticals include financial services and banking (10% of new programs), followed by media and entertainment (10%) retail and ecommerce (6%), and travel and hospitality (3%).
In April 2016, the first bug bounty program in the history of the U.S. federal government launched with the Department of Defense’s Hack the Pentagon followed by the U.S. Army, U.S. Air Force, GSA’s Technology Transformation Service, and the Internal Revenue Service. In late May 2017, U.S. Senators introduced a bill to establish a federal bug bounty program in the Department of Homeland Security. The U.K. government also announced a vulnerability disclosure policy pilot. These actions suggest that hacker-powered programs are increasingly viewed as vital for securing digital assets for the public sector.
With 76 percent, ecommerce and retail had the most significant adoption rates year-over-year. Gaming came in second with 75 percent. This was measured as overall growth in hacker-powered security adoption from January 1, 2016 to May 31, 2017.
There has been a 46 percent increase year over year in publicly disclosed vulnerability reports. These disclosed vulnerability reports in many cases are available in their entirety for anyone to learn from.
Fast Time to Resolution
Seventy-seven percent of all bug bounty programs have their first vulnerability reported in the first 24 hours. For the U.S. Army, it only took five minutes. Once a customer has confirmed the vulnerability is valid, they have the opportunity to reward the hacker and fix the issue. HackerOne tracks the time to resolution for all programs. A speedy resolution not only helps protect the organization and its customers faster (by fixing the issue), it also helps attract hackers to the customer’s program (by paying hackers faster).
Our data demonstrates that the top performing programs on HackerOne (based on the HackerOne Success Index) attract not only more overall hackers but more repeat hackers. Repeat hackers are responsible for the majority of resolved reports and bounties on the HackerOne platform. The more time a hacker spends looking at your software, the more valuable the reports are likely to be. This indicates there is significant value in building hacker loyalty.
Based on time to resolution data in the HackerOne platform, ecommerce and retail businesses are the fastest at resolving vulnerabilities, taking a total of 31 days on average. Education organizations are the next fastest, resolving vulnerabilities in 33 days on average. Certain industries resolve issues more slowly, particularly in highly regulated areas with complex software stacks and supply chains, such as telecommunications and government.

Bounty Payouts Vary Across Industry
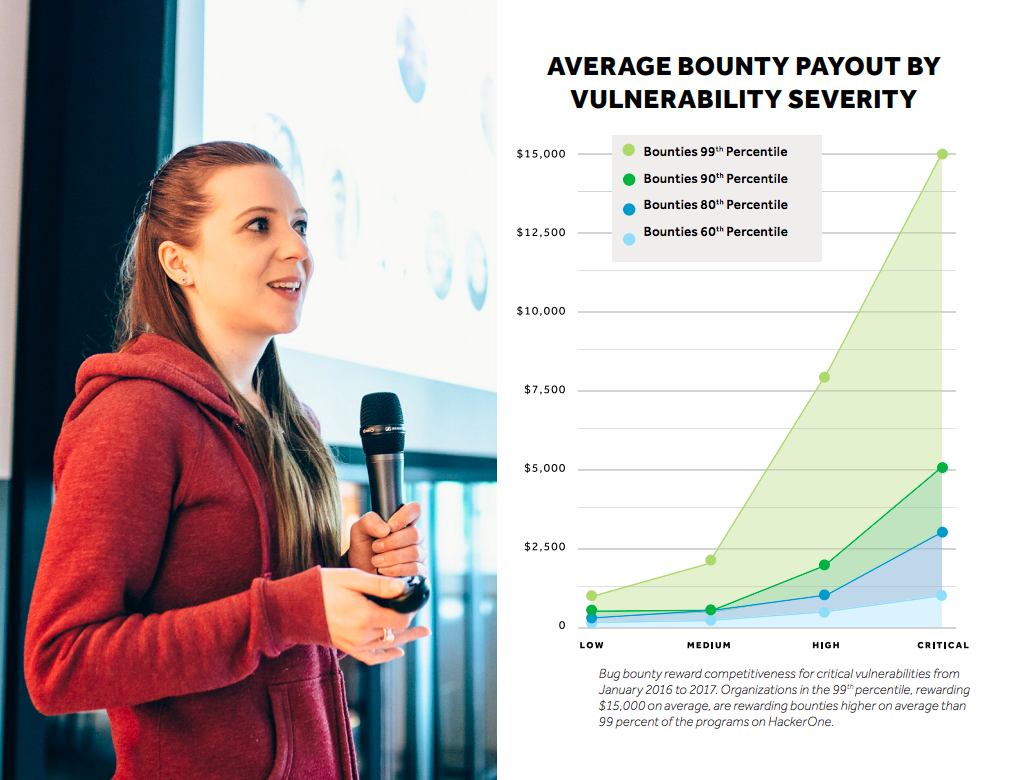
Bug bounty programs on the HackerOne platform that reward $15,000 on average for critical vulnerabilities are in the top 1% of reward competitiveness. Those programs reward higher bounties than 99 percent of the programs on HackerOne. In comparison 60% of organizations on the platform reward $1,000 on average for critical vulnerabilities.
Bug bounty programs will pay average or below average, bounties when they first launch. As the organization fixes more vulnerabilities and their attack surface hardens, bounty payouts should increase over time. In most cases, critical vulnerabilities are harder to find in an organization that pays $30,000 on average, than in an organization that pays $1,000 on average.
Hardening your attack surface and increasing reward competitiveness takes time and sustained effort. For example, Google Chrome steadily increased their top bounty from $3,000 to $100,000 over the course of more than five years. Bug bounty programs offering bounties in the top 1 percent get there by continuously working with hackers to improve security.
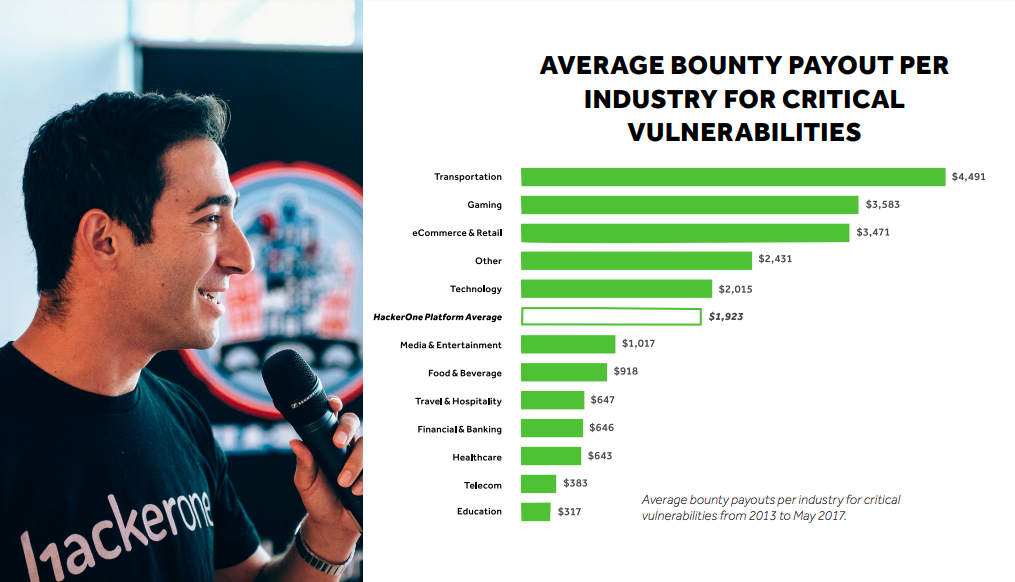
Looking at bounty averages by industry for critical issues, the highest average payments come from transportation ($4,491), followed by gaming ($3,583). Through May 2017, the average bounty for a critical issue paid to hackers on the HackerOne Platform was $1,923. For all vulnerabilities reported of any severity, the average bounty payout was $467.
Vulnerabilities submitted by hackers are ranked either low, medium, high or critical as part of the scoring process. Averages are from May 2016 to May 2017. HackerOne uses the Common Vulnerability Scoring System (CVSS) 3.0 calculator to assign severity.
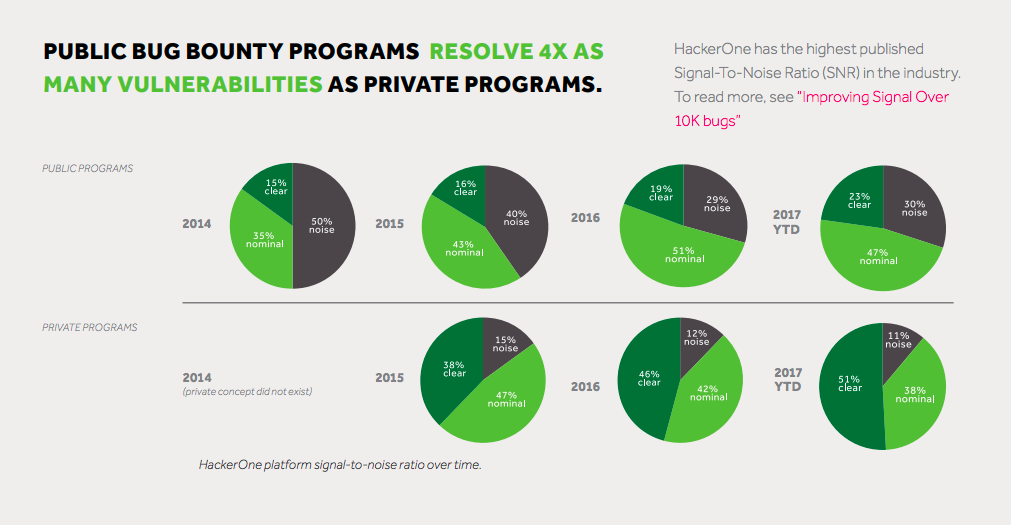
Public Bounties Resolve 4x More Vulnerabilities
Private bug bounty programs make up 88 percent of all bug bounty programs on HackerOne and 92 percent of the bug bounty programs launched in 2016. The majority of public bug bounty programs are from technology (64%) followed by financial services and banking (11%) and media and entertainment (8%). In contrast, 100 percent of programs are private in the travel and hospitality, healthcare, insurance, aviation, and telecommunications industries.
While public programs made up only eight percent of HackerOne bug bounty launches in the past 12 months, public programs pay bounties and resolve issues at four times the rate of private programs.
Market Leaders Embrace Vulnerability Disclosure Policies
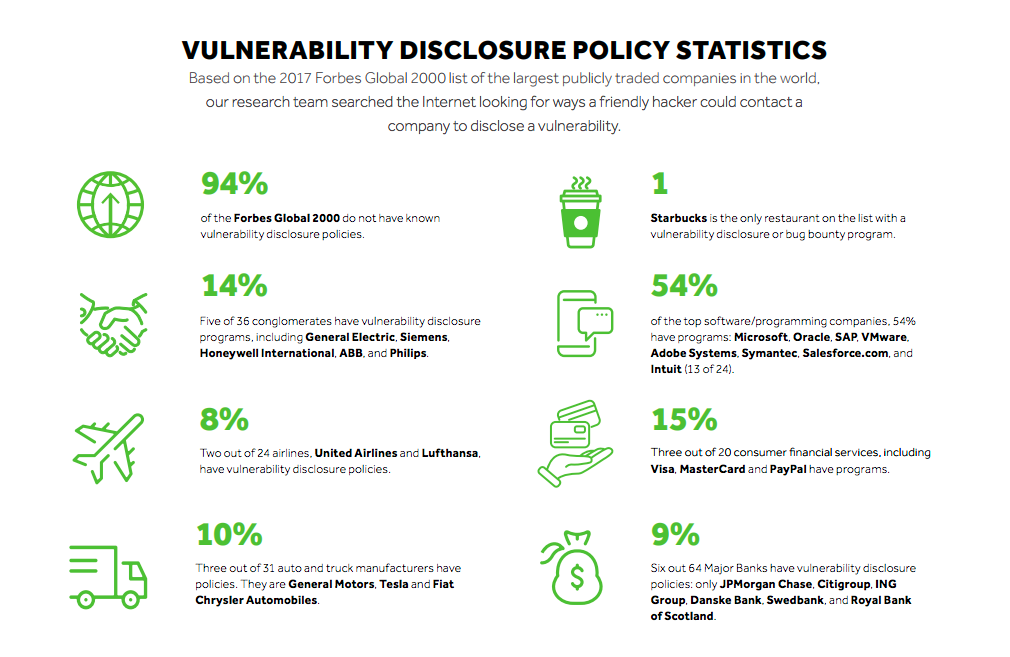
Today, with thousands of organizations encouraging ethical hacking, 94 percent of the Forbes Global 2000 do not have known vulnerability disclosure policies despite guidance from the United States Department of Defense, Food and Drug Administration, National Highway Traffic Safety Administration, National Telecommunications and Information Administration, National Institute of Standards and Technology, and Federal Trade Commission — to name a few. Nearly 200 organizations rely on the HackerOne platform for their VDP, including the The U.S. Department of Defense, LinkedIn, NewRelic and General Motors.
Given the increased concern about IoT and connected device security, Panasonic is the only consumer electronics company with a public VDP on the Forbes Global 2000 list. Major industry conglomerates, including General Electric, Siemens, Honeywell International, ABB, and Philips, have public policies. Over 50 percent of the Forbes top software/programming companies have a VDP and in many cases offer hackers incentives with bug bounty programs, including Microsoft, Snapchat, Adobe, Symantec, Salesforce.com, and Intuit.
Starbucks is the only restaurant on the list with a VDP. Another major restaurant company, McDonald’s, made the news in January 2017 due to its lack of a clear VDP. In retail, Home Depot also does not have a policy, even after agreeing to a $25 million settlement for its 2014 security breach that impacted 50 million customers.
_______________________________________
Read on for other trends and data in the Hacker-Powered Security Report 2017.
HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited. As the contemporary alternative to traditional penetration testing, our bug bounty program solutions encompass vulnerability assessment, crowdsourced testing and responsible disclosure management. Discover more about our security testing solutions or Contact Us today.


