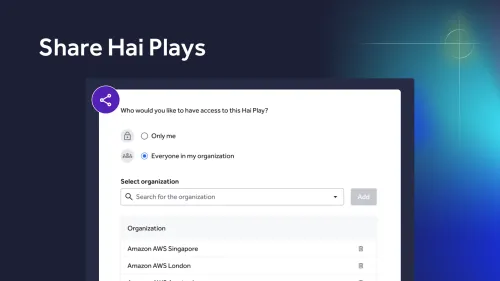
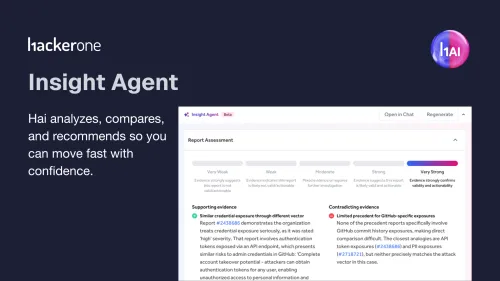
Internal triage sounds simple, but volume and noise break workflows. Compare in-house vs expert triage for validated signal, faster fixes, and reduced risk.
HackerOne Blog
Exposure Management
Image

Security leaders forecast 2026 as the year CTEM becomes essential, with AI-driven threats, agentic security, and continuous validation reshaping cyber risk.