Your always-on vulnerability disclosure program
Establish a direct channel for external parties to report discovered vulnerabilities before malicious actors do.
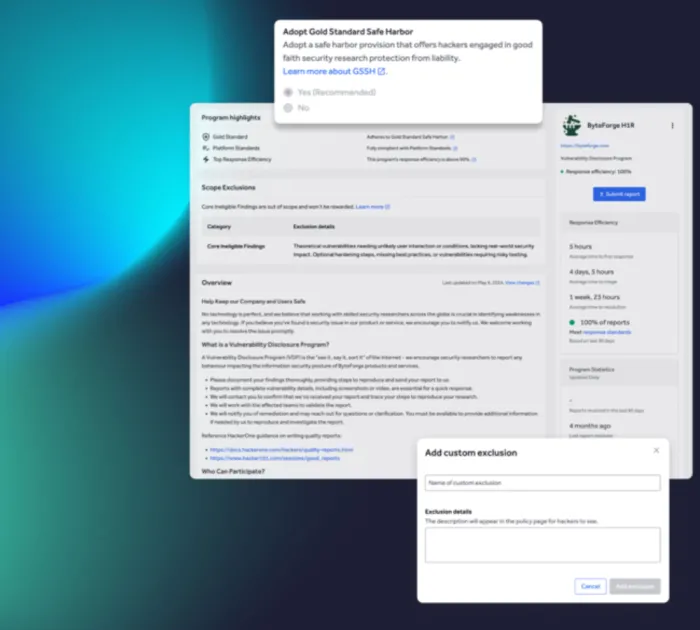
Create disclosure guidelines
Equip external parties with clear guidelines and expectations for reporting vulnerabilities, ensuring a smooth and confident process.
- Accelerate vulnerability identification and remediation with efficient capturing and tracking of reports.
- Benefits from in-platform advice and templates for policy creation based on best practices from thousands of programs.
- Choose your hosting option: HackerOne's site, email-based, or on your own domain.
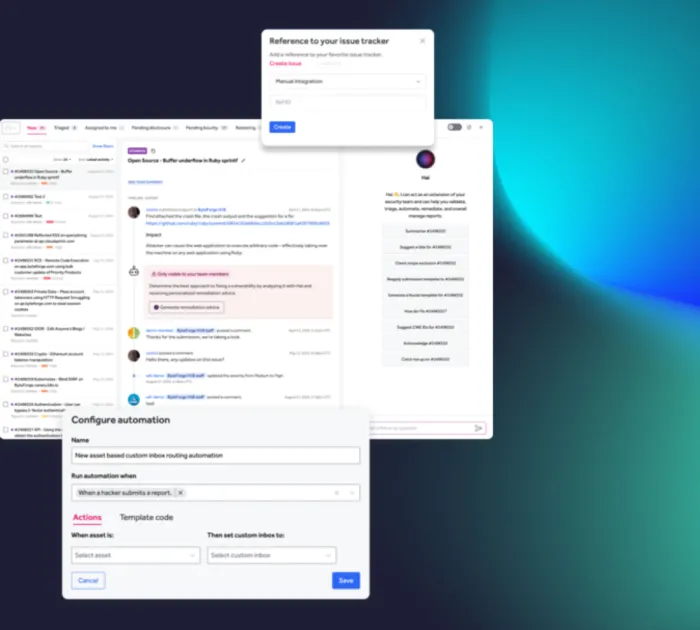
Streamline workflows
Simplify vulnerability management with workflows that support your SDLC and prioritize reports based on CVSS levels.
- Set up workflows with custom inboxes, advanced filters and automations for easy prioritization of vulnerabilities.
- Rely on HackerOne's Hai and triage team to validate vulnerabilities and cut through the noise.
- Connect directly with DevOps and security tools to integrate triaged findings into your SDLC for efficient remediation.
Optimize decision making
Understand your security posture and make informed decisions based on data from vulnerability submissions.
- Utilize our advanced dashboards and reports to track and understand vulnerability trends.
- Access tools for reporting, analysis, and integration to optimize your security processes.
- Identify asset types with the most vulnerabilities and track the longest-open vulnerability reports to improve the mean time to remediation.
Maintain compliance
Support adherence to industry standards and legal requirements with comprehensive VDP management.
- Simplify compliance reporting with built-in attestation reports, demonstrating your commitment to security practices.
- Continuously monitor and update your VDP to meet evolving regulatory demands and frameworks.
- Instantly access detailed reports to support audits and prove compliance with common frameworks and mandates.
Triage services
Our in-house security analysts validate and prioritize all incoming vulnerability reports and maintain ongoing communication with hackers—zeroing out the noise while providing actionable insights to your team.
Security advisory services
Manage and scale your program with best practices and insights from experts in cyber risk reduction. Our solutions architects help tailor your program—from custom workflows to KPIs for measuring program success.