How much is a bug worth? Introducing Bounty Statistics

Ever wondered how much you should reward a hacker? Too little and you risk offense, too much and you set the wrong expectations. What do other programs tend to pay for a particular vulnerability? Today, HackerOne gives you this insight with Bounty Statistics.
Over the course of bug bounty history, opinions have fluctuated on what a specific report can be worth. From “Mr. Woodbridge” offering $500 for a picked lock, to Hunter & Ready offering up a Volkswagen Beetle. On HackerOne, companies have awarded over 11,000 bounties and counting, for everything from hypothetical issues to mission-critical systems.
After a considerable beta period, HackerOne is proud to publicly launch “Bounty Statistics”. We have collated the data from our 500+ bounty paying programs, and will show you the results every time you award a bounty!
Integrated with the recently launched CVSS severity setting on reports, we will now automatically show you the median bounty across our platform for that severity, as well as what programs at a competitive and top level are paying out.
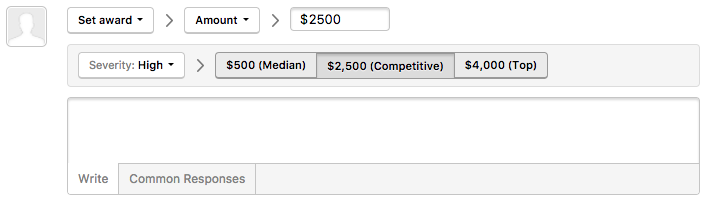 Competitive bounty level for a High severity report
Competitive bounty level for a High severity report
These statistics can help you gauge your reward competitiveness, as well as help you be as consistent as possible in awarding bounties! Please let us know what you think, and if/how bounty statistics helped you at feedback@hackerone.com, or on Twitter - @hacker0x01.
- Dirk Zittersteyn, Philip Kocanda and the HackerOne team.
HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited. As the contemporary alternative to traditional penetration testing, our bug bounty program solutions encompass vulnerability assessment, crowdsourced testing and responsible disclosure management. Discover more about our security testing solutions or Contact Us today.


