How2Hack - Get Started Hacking Mobile

While hunting for bug bounties, attack surface plays a major role. Hacking on mobile adds more juicy attack surface and increases your likelihood of finding new endpoints… and bugs! For example, some applications use different API endpoints for mobile users, as well as use different endpoints for each platform. Mobile apps are likely to get less attention compared to the web applications or the domains that are in the scope of a program. Setting up a mobile lab for the first time can be confusing and exhausting. This blog will help you quickly learn how to get started on mobile hacking, for Android and iOS, by covering the following topics:
- Installing the Android SDK
- Setting up and launching a Virtual Device
- Downloading an APK file from the Google Store.
- Installing the APK on your Virtual Device
- Setting up Burp Suite with a Virtual Device
- Decompiling an APK file to extract the source code
Set Up A Virtual Android Device
First, you’ll need to get the latest version of Android Studio https://developer.android.com/sdk/index.html
Next, create an Android Virtual Device(AVD) by clicking
Tools > Android > AVD Manager > Create a Virtual Android Device.
Protip: it’s crucial to keep your virtual device up to date on patches in order to avoid any compatibility problems with apps you want to hack on. Now you are ready to run your Android Virtual Device and download your first Android Application.
Lucky for us, most bounty programs include a link to the app that looks like this: https://play.google.com/store/apps/details?id=com.*.android.*.*
Now we can look up an Android APK Downloader, provide the above link to it, and download the APK. In order to instal the app on your device, you’ll need the Android Debugging Bridge (adb) which comes with the Android Studio SDK.
Pro-tip: It’s best to create an alias in your .bash_profile file by inserting the following line to the top:
[code]
alias adb='/Users/YOUR_USERNAME/Library/Android/sdk/platform-tools/adb'
[/code]
Now save the changes and execute the following command to put that in effect:
$ source ~/.bash_profile
Now we are ready to install our APK file by executing the command below:
$ adb install /path/to/the/app/com.yourapp.apk
Setting up the Proxy
You’ll need to configure the Emulator to communicate with your intercepting proxy tool. In this example, we’ll use Burp Suite. In order to intercept the encrypted traffic between the app and the server, you’ll first need to setup a proxy listener on your computer by doing the following:
Go to the Options tab under the Proxy tab in Burp Suite:
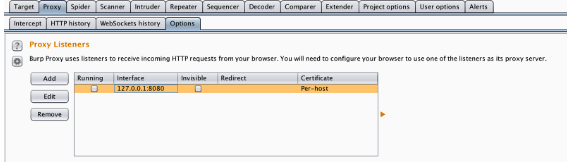
Click on Add, provide it a port number such as 8080, change the specific address to the IP address of your computer, and hit ok:

At this point, your proxy listener is up and running on your computer. Remember the IP address of your computer; you’ll need to use it when configuring your phone or virtual device, so traffic from your phone/virtual device can “point” to your computer, where you can intercept the traffic with Burp Suite.
Installing Burp Certificate on an Android Device:
- Now that your proxy listener is running, browse to http://burp on your computer.
- Click on CA Certificate and rename the downloaded file to something easy to remember.
- Send the cert as an attachment to an email address you can access on the Android device.
- Download the attachment from your Android device.
- On your device browse to the file to find the path to the .cer file (i.e.: Download/mycert.cer)
- Go to your Security settings, click on Credential storage, provide a name, and install the certificate.
- Change the proxy settings (WiFi -> Modify Network Config -> Manual) on your device and point it to your computer’s IP address, including the port number you defined in the proxy tab in Burp Suite. At this point, traffic in your phone should be redirected to the proxy listener (Burp Suite) on your computer.
Installing Burp Certificate on an iOS Device:
- Go to your WiFi settings -> click on the information (i) icon -> Scroll down to the HTTP proxy settings -> point it to our IP address and port number from the proxy tab in Burp Suite.
- Make sure burp is monitoring and intercepting your iOS device’s traffic and browse to http://burp using Safari.
- Click on the “CA Certificate” link and install the certificate
Now, you should be able to browse from your mobile device without any security warnings.
Note: Once you are done testing, especially if this is a mobile device you use regularly, it’s a good idea to remove the cert. If someone else were to make a similar certificate and MITM you, you wouldn’t get a warning!
Getting to the Source
Now you are ready to intercept requests sent by mobile apps and check for vulnerabilities... but why stop there? You can increase your chances of uncovering vulnerabilities if you have access to the source. Lucky for us, we are able to access the APK source, since the APK files are similar in nature to compressed archive files, such as ZIPs. You can uncompress an APK by using tools made for that purpose (e.g. unzip or 7-zip)… or you can just rename the file to .zip instead of .apk to make things much easier!
After uncompressing your APK file, the uncompressed folder should look similar to the figure below:
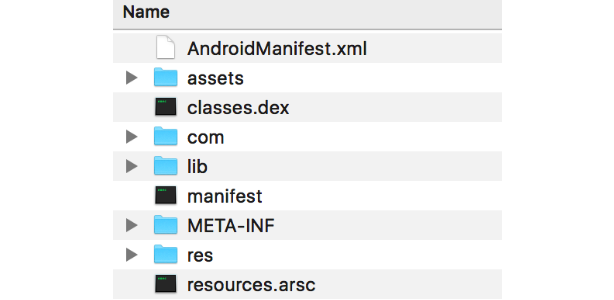
You can read all the details about the APK file structure here, but for this tutorial we are going to focus specifically on the classes.dex file. Android apps are written in Java, then get compiled to bytecode for the Java virtual machine, which is then translated to Dalvik bytecode, and finally stored as a classes.dex file.
In order for us to decompile and get access the source code, we are going to use a tool called dex2jar. Dex2jar allows us to decompile the dex files into (almost) readable .class files packed with a JAR extension. After downloading dex2jar, move it to your mobile application pentesting directory so you can have it handy every time you look at a new app. Using the command below, we are going to decompile and convert our dex file to a jar file.
$ ./dex2jar.sh /path/to/app/classes.dex
Now using JD-GUI, we can open up our JAR file, access the source code, and look for hardcoded passwords, private keys, and more!
Once you have your mobile hacking station ready, join the fun and #Hacktheworld!
Have questions or suggestions! You can reach us at Hackers@hackerone.com
A big thank you to Patrik Fehrenbach for his tips that helped me put this tutorial together.
HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited. As the contemporary alternative to traditional penetration testing, our bug bounty program solutions encompass vulnerability assessment, crowdsourced testing and responsible disclosure management. Discover more about our security testing solutions or Contact Us today.