Q&A With PortSwigger's James Kettle: Bug Bounties, Exploit Stories, and More!

As 2016 came to a slow-burning close, the gang at PortSwigger debuted its public bug bounty program on HackerOne. We’re super excited to be partnering with them. Their program’s attack surface covers the latest versions of their popular Burp Suite web app testing platform and portswigger.net.
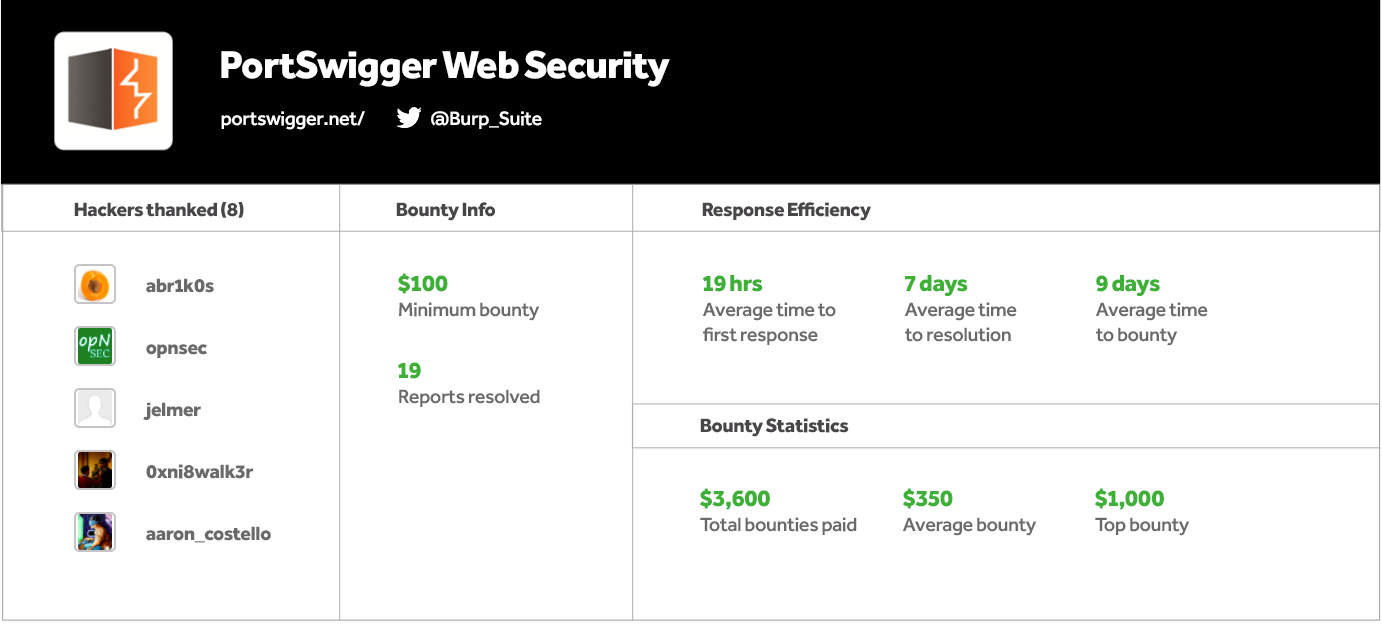 PortSwigger's Current Bounty Statistics
PortSwigger's Current Bounty Statistics
Burp Suite’s integrated platform features a full complement of tools that support every step of testing. It includes an advanced web app scanner that automates many different kinds of vulnerabilities, and an intruder tool that adds power to the search for complex vulnerabilities.
In short, it’s a hacker’s best friend.
We sat down with James Kettle, PortSwigger’s Head of Research, to get the scoop on their public bounty program, and to learn how clarity helps keep their hackers happy. Make sure to stick around 'til the end where company founder Dafydd Stuttard explains the meaning behind their company and product name!
Q: Tell us about yourself!
I’m Head of Research at PortSwigger – I devise new ways of automating hacking techniques for Burp Suite, and occasionally new vulnerability classes.
Q: Briefly describe your company / product
PortSwigger Web Security is the maker of Burp Suite, a wildly popular toolkit for in-depth manual and automated security testing of websites and web services. Supported by our huge global user-base, over the last decade we've frequently advanced the boundaries of web security tools from our headquarters in the UK.
Q: You recently launched your bug bounty program on HackerOne: The first question we have is: why did you launch a bug bounty program in the first place?
I’ve done quite a lot of bug bounty hunting myself over the years, and I feel a bug bounty program is a natural next step for any company with a mature security program and a public attack surface. For us it’s also an extra way to engage with the security community, which is a bonus.
Q: You started off with a private program (which is what we recommend) Why did you decide to go public after a few months?
We always planned to go public - it means if any of our ingenious users happen to ‘accidentally’ find a vulnerability in Burp, they know we’ll be happy to hear about it. Also, having a public bug bounty demonstrates a confidence in your security that anyone selling a security tool should have.
Q: You guys are a security-focused company, your product is pretty much a mandatory tool in the hacker toolbelt… So you do lots of things to keep your product secure, but how does your bug bounty program supplement the work you guys do?
As a proxy, Burp Suite offers an interesting and unusual attack surface and the bug bounty has proven to be a great source of novel attack ideas. We’ve just implemented some broad mitigations as a direct result of recent submissions.
It also means the security community can hold us accountable; it’s harder to postpone fixing a low severity issue when you know it’s only a matter of time until someone else hunts it down and reports it.
Q: You guys know hackers pretty well. When launching your bug bounty program what are some things you’ve done to keep your invited hackers happy?
I spent a lot of time on the bounty brief; my goal is that anyone who reads the brief will know what outcome to expect from a given submission. I think people especially like the ‘known issues’ section as it saves them from wasting time reporting something that we already know about. Other than that, our speedy response times are certainly appreciated.
Q: Okay, let’s role play for a minute: Your buddy, a co-founder of another company, is thinking of starting a bug bounty program. He asks you why he should have a bug bounty program - what do you say to him?
People are already trying to hack your product, starting a bug bounty program just means you’ll get to see what some of them find.
Q: Let’s talk data and stats: What do you look at? Any stats in particular you’re interested in?
The key stat for us is the ratio of resolved bugs to submitted bugs (ie, our signal to noise ratio). We’ve managed to significantly improve this ratio by using your macro feature to display a warning when people try to submit common lame or out of scope issues.
Q: Let us brag about you a little bit; you’ve got a really good response time thus far (in the 90th percentile): how do you manage your team to be so efficient? Any tips you can provide to other security teams out there?
Well, I’m sure being a security company helps - we have no shortage of expertise or enthusiasm to evaluate reports. That said, I think the most important thing is a well-crafted brief. If you can speedily close every invalid submission with a reference to the brief, that frees your time for the juicy issues.
Q: Okay - so we have to ask this; please give us all the juicy details ;) - Why did you choose HackerOne as your bug bounty platform provider?
I love the reputation/signal system; it influences disruptive hacker behaviour and also helps us evaluate how seriously we should take some of the weirder submissions we get. I actually posted a review of the leading platforms from a bounty hunter’s perspective a few months ago.
Q: Do you have any fun hacker stories? Any amazing personal hacking experiences or ways hackers have used Burp Suite that you’d like to share?
I save my best stories for presentations but I recently audited a site where the password reset functionality required that you enter a username and an email address in a single form. It then looked up the attacker-supplied username, and emailed the password to the attacker-supplied email address. This was on a site that had been tested multiple times before by several different companies! I think the only moral we can take from this is that some vulnerabilities are so obvious they’re hard to see.
Q: Anything else you want to share with us or our community?
I’ve encountered a recurring misconception that bug bounties are an attempt by vendors to outbid the black market for exploits, or ought to match the potential damage a vulnerability could do. This ignores the simple fact that many hackers would rather see vulnerabilities patched than exploited for profit.
Enter Dafydd Studdard, PortSwigger founder and author of The Web Application Hacker’s Handbook
BONUS Q: You guys have such a unique name, can you tell us why "Burp Suite" and why "PortSwigger" are your chosen monikers?
PortSwigger was a play on the networking term "port." When I started hacking, it was mostly focused on the network/infrastructure layer, and many of the tools had the word "port" in them - things like "port scanner". I chose "PortSwigger" as a pun on the term, and it means someone who likes to drink port.
Burp was just a random name I came up with on the day I started working on the tool. At that time, I often started work on small coding projects that didn't ultimately go anywhere, and Burp was just another project like those. I didn't think for a minute that it would become what it is today, and consequently didn't put any thought into the name.
Join PortSwigger and over 700 other companies making the internet safer with hacker-powered security. Get started with your own vulnerability disclosure program or bug bounty journey.
HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited. As the contemporary alternative to traditional penetration testing, our bug bounty program solutions encompass vulnerability assessment, crowdsourced testing and responsible disclosure management. Discover more about our security testing solutions or Contact Us today.


