Hackers have earned more than $50M in bug bounty cash on HackerOne: Time to celebrate!

Hacking has a storied history. Hackers have always been curious people searching for new and creative ways to understand, deconstruct, and yes break systems. This intense creativity and the positive power it brings is perfectly evident in bug bounty. In just 7 years, hackers on HackerOne have managed to make the internet safer by reporting over 120,000 vulnerabilities to over 1,300 programs earning more than $50,000,000. Hackers have been embraced by organizations in all industries, and bounties have acted as multipliers of good in their communities.
How do you celebrate with hackers? You issue a challenge.

To celebrate $50M in bounties, we announced our hardest, most advanced CTF ever which presented challenges spanning from mobile, crypto, and the web. Hackers had to first hunt down the “HackerOne Thermostat” app, break into the backend, and find their way into the thermostat itself to finally get into the accounting server to steal the flag. This graphic by @manoelt says it all:
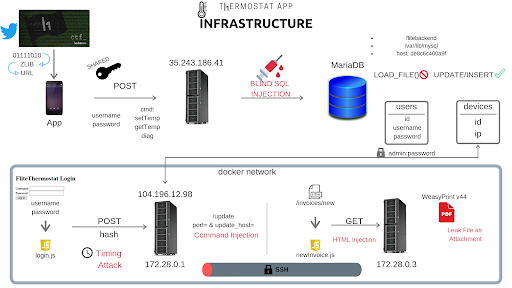
Hundreds of hackers participated, but only a select few were able to make it all the way to the end. This was the first time we created a dedicated space, a channel on our Discord server, for folks to chat about one of our big CTFs. It was thrilling to watch thousands of messages fly back and forth, especially as hackers hit one of our favorite red herrings, a fake SQL parser. The results really speak for themselves; we received so many outstanding submissions and saw more creativity than ever before.
When you have such an epic challenge, you need an epic prize.
The first to solve the challenge was eligible for a $10k prize and an invitation to Las Vegas for the h1-702 2019 live hacking event. The best 5 reports from those who solved the challenge are also heading to Las Vegas to participate in h1-702!
In the end, 16 hackers successfully completed the CTF and choosing winners from the field of reports was quite difficult. With so many components to the CTF, there were many areas where a report could shine in different, fun ways.
And the winners are...
Our grand prize winner was BitK, beating the rest of the field by over 24 hours!
Below are all of our winners with a mini description about what we appreciated about their reports.Great work by all!
This hacker was responsible for the impressive diagram above, which really shows the care and attention that was put into this challenge. The entire report is a pleasure to read and we believe there’s a lot to learn from it.
These hackers worked together and the results are stunning, with their thought process clearly laid out in the report and solid teamwork throughout. We especially loved that they represented the timing attack and included a CWE for each vuln in the chain.
In this report, we particularly appreciated that the tool output was included in the way it was. This report let us really get an understanding of how the hacker approached the problem. Additionally, this was one of only two reports to have correctly labeled the severity, when taking into consideration the business risk: none!
This report was simply beautiful and professional throughout, with everything clearly explained and laid out in a form that was easy and pleasant to read. Additionally, ajxchapman discussed how he used OCR to read the binary out of the image; that level of dedication alone deserves to be recognized. Finally, we love that every script used was shared in the report so we could replicate his results!
Unlike any other reports submitted for this CTF, this report is written as if it were being reported to a real bug bounty program in the wild. Because of this, it’s quick, straight to the point, and gives absolutely everything necessary to easily understand and reproduce the exploits. We couldn’t help but appreciate this unique approach to a CTF write-up.
Congrats to @BitK and ALL the incredible hackers! We could not be more happy with the results we got from our amazing community and we’re so excited to see all of them (and hopefully many of you reading this) at the biggest live hacking event of the year in Las Vegas in a few months. Get psyched watching our recap of last year!


