Crowdsourced Security ROI (RoM): How to Measure Return on Mitigation
Crowdsourced security delivers value that goes beyond just finding bugs: it helps reduce risk, strengthen trust, and avoid potential losses.
Return on Mitigation (RoM) is a way to quantify that value, measuring how much cost or damage your organization prevents through proactive, researcher-led vulnerability discovery and remediation.
What is Return on Mitigation?
RoM is a metric that compares the value of mitigated losses (what could’ve gone wrong and didn’t) against the costs you incurred to make that happen (bounty payments, pentesting, internal remediation, etc.).
Traditional ROI looks at revenue vs. cost. RoM flips this view to show value in loss prevention. It’s especially useful for cybersecurity where many investments don’t directly generate revenue but protect what matters.
Elements that RoM evaluates:
- Severity
- Likelihood
- Exposure
- Cost of mitigation
The Challenge of Calculating Cybersecurity Investments
Measuring the value of cybersecurity investments is rarely straightforward. Many of the benefits come from avoided incidents, which makes them harder to quantify. Intangible costs, uncertain probabilities, and fragmented data all complicate the calculation.
Some of the biggest hurdles include:
- Intangible costs & lack of visibility: Losses from reputational harm, trust erosion, regulatory penalties are hard to estimate ahead of time.
- Uncertainty in threat likelihood: How likely is a vulnerability to be exploited? What’s the exposure window? These variables are often difficult to pin down.
- Fragmented costs: Between internal engineering, external researchers, program overhead, verification, remediation—tallying all costs can get messy.
- Traditional metrics fall short: ROI metrics often don’t accommodate “what didn’t happen”, such as missed breaches or avoided exploits.
How to Measure Return on Mitigation
The formula for Return on Mitigation is visualized as:
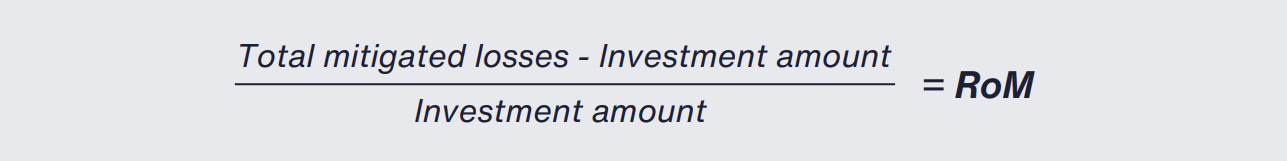
Data should be gathered to inform these components. Here is a step‑by‑step model to calculate RoM:
| Component | What to Collect / Estimate |
|---|---|
| Mitigated Losses | Estimate financial impact avoided: breach cost, regulatory fines, downtime, brand damage. Use case examples (e.g. critical and high-severity findings) can help. |
| Cost of Mitigation | Include all relevant costs: researcher payments, internal remediation engineering, verification, program management overhead. |
| Severity, Likelihood & Exposure | Classify issues by severity; assess how likely they were to be exploited; determine exposure (how accessible the vulnerability was). |
| Time Frame | Over what period did you measure mitigated losses vs. costs (year, quarter, program season). |
| Comparisons & Benchmarks | Compare RoM across programs (bug bounty vs pentest vs VDP), versus traditional security spend, or industry averages. Tools like the RoM dashboard help with exportable summaries that make this visible. |
Seeing a high RoM helps make a strong case with leadership and justify further investment.
Frequently asked questions
They are related, but different. ROI measures gains vs cost (profit). RoM measures prevented losses vs cost. It’s about risk reduction and what you’ve avoided.
Accuracy depends on good data: costs, threat models, likelihood estimates. Even rough estimates are valuable if assumptions are transparent.
Use ranges, historical data, or industry benchmarks. Sensitivity analyses can help demonstrate different outcomes.
No. High or critical vulnerabilities with broad exposure usually account for most of the mitigated losses. Lower‑severity or duplicate issues contribute less, though duplicates still offer validation value.
Quarterly is a common cadence for RoM, or it can be performed annually for budgeting. The RoM Dashboard makes it easier to generate exportable summaries for regular reviews.
Use RoM to demonstrate business value, compare security investments, prioritize remediation, align goals with exposure, and present risk reduction in financial terms.