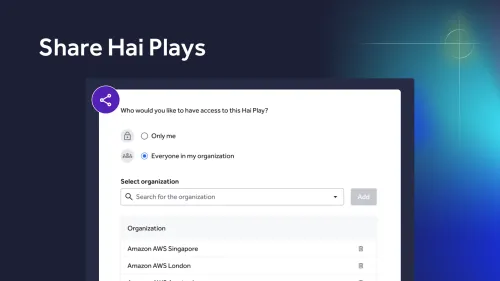
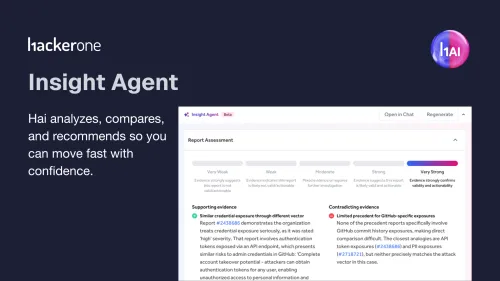
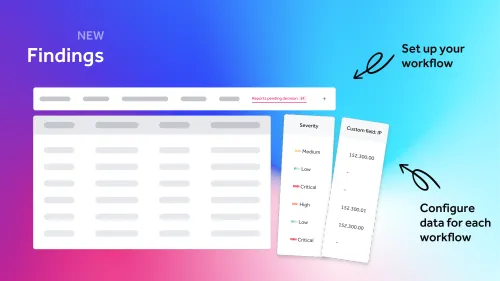
Security leaders forecast 2026 as the year CTEM becomes essential, with AI-driven threats, agentic security, and continuous validation reshaping cyber risk.
HackerOne Blog
Exposure Management
Image
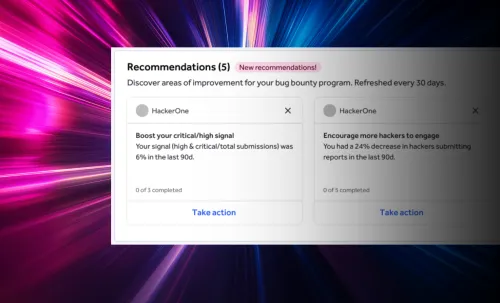
What if your security program could self-optimize? With HackerOne Recommendations, it can.