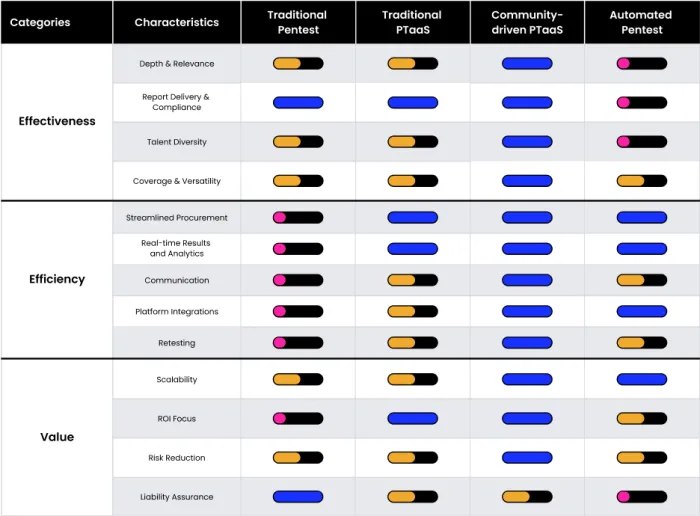
Which Pentesting Method Is Right For You?
Different pentest methodologies offer different benefits, and many of the more “traditional” methods seem redundant or are cumbersome to manage. Given the variety of models, vendors, and methodologies available, how do organizations like yours pinpoint the ideal pentest for your needs? Learn how with the Pentest Matrix.
Pentesting Options
Traditional Pentesting via Consultancies
Delivered by professional service providers using in-house salaried pentesters or long-term contractors
Delivered by professional service providers using in-house salaried pentesters or long-term contractors
Traditional Pentesting as a Service (PTaaS)
Traditional pentesting with an added user interface, leveraging in-house salaried pentesters or long-term contractors
Traditional pentesting with an added user interface, leveraging in-house salaried pentesters or long-term contractors
Automated Pentesting
Uses predefined scripts or tools to systematically scan and assess systems for vulnerabilities based on recognized signatures or patterns
Uses predefined scripts or tools to systematically scan and assess systems for vulnerabilities based on recognized signatures or patterns
Community-driven PTaaS
Modern evolution of pentesting, harnessing the collective expertise of a global community of vetted security researchers
Modern evolution of pentesting, harnessing the collective expertise of a global community of vetted security researchers
What Makes an Ideal Pentest?
An ideal pentest ensures both security coverage and compliance by uncovering critical vulnerabilities and educating your engineering team to enhance security best practices. Traditional consultancy-based pentesting struggles to meet these goals.
Why? Because the targeted environment no longer exists. The static, predictable release cycles of the past have given way to dynamic, rapidly changing attack surfaces. Point-in-time assessments are increasingly outpaced by constantly evolving threat actors and tactics, leaving many organizations exposed. Traditional pentesting, while still useful in limited scenarios, is quickly becoming obsolete.
Power of Community-
driven PTaaS

What Sets HackerOne's
Pentesters Apart