Adversarial Exposure Validation (AEV)
Prove what’s really exploitable in your business environments
Bridging Automation & Expertise
Security teams face a constant balancing act. Traditional SAST and DAST tools provide broad visibility but often overwhelm teams with unverified findings. Expert-led testing delivers invaluable depth and creativity, yet it happens only periodically by design. To achieve effective exposure management, organizations need both—the scale and speed of automation combined with the insight and ingenuity of human expertise. The real challenge lies in connecting these approaches into a continuous, evidence-based view of risk.
Adversarial Exposure Validation (AEV) is a new standard in offensive security testing. It uses autonomous, AI-driven agents to mirror how attackers operate, continuously simulating real-world attackers at machine speed and validating exploitability in real time. AEV provides the connective layer — validating exploitability continuously, at scale.
Validate real risk continuously
Move from theoretical vulnerabilities to confirmed, exploitable weaknesses.
Move from theoretical vulnerabilities to confirmed, exploitable weaknesses.
Reduce noise and focus effort
Cut through false positives and prioritize what truly matters.
Cut through false positives and prioritize what truly matters.
Accelerate resilience
Combine automation’s scale with human creativity for faster, smarter remediation.
Combine automation’s scale with human creativity for faster, smarter remediation.
HackerOne Platform
Just as defenders layer controls, offensive security requires layered testing. HackerOne brings together automation, validation, and human expertise into a single offensive security platform so you don’t have to choose between speed and depth.
Pre-production application security that identifies issues at the source.
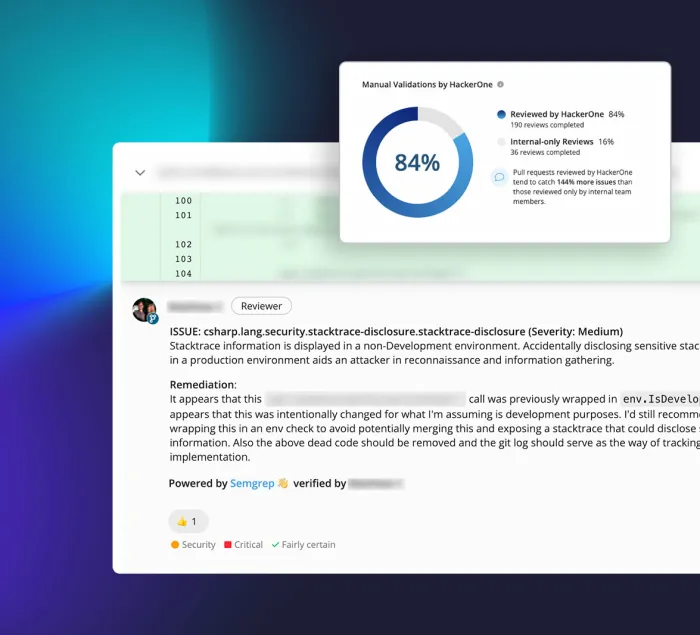
HackerOne Code combines AI and human experts to catch vulnerabilities before they become exploitable, and embeds remediation guidance directly into developer workflows. Every time code changes, the platform re-validates automatically, ensuring that previous fixes remain effective and new risks are quickly flagged.
Autonomous, discovery of vulnerabilities and scenario-based validation of exploits.
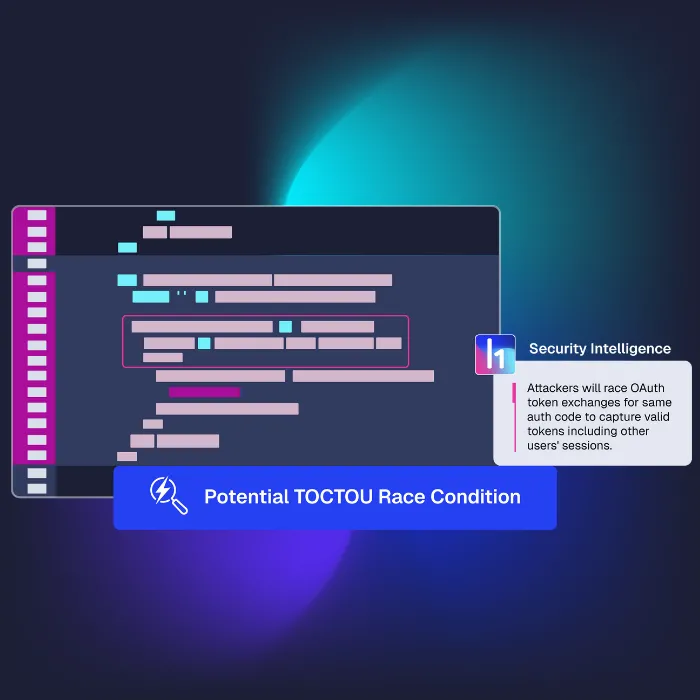
Between scheduled testing, blind spots often emerge — and adversaries know how to exploit them. HackerOne’s agentic pentesting fills these gaps with autonomous, AI-driven agents that continuously simulate attacker behavior at machine speed. Combined with human validation, it delivers evidence-based findings that prove exploitability under real-world runtime conditions.
Human ingenuity where it matters most.
Not all vulnerabilities can be discovered or validated by automation. That’s why HackerOne connects organizations to the world’s largest community of security researchers and vetted pentesters to help uncover sophisticated attack paths that scanners and AI agents simply cannot detect. Human testers bring critical context, demonstrating exploitability in business-specific scenarios and validating issues that matter most to the organization’s unique environment.

Why HackerOne for AEV?
Domain expertise & depth
HackerOne gives organizations access to the world’s largest community of security researchers, delivering unmatched human creativity and contextual insight. Our experts surface vulnerabilities that scanners and automation cannot.
The Hai advantage
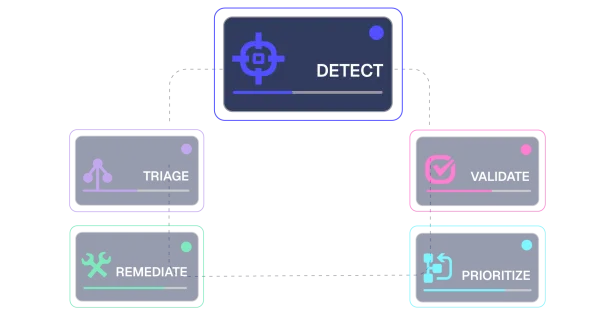
The Hai Agentic System continuously orchestrates validation, prioritization, and remediation, closing the loop across the entire CTEM lifecycle and transforming the path from discovery to risk reduction into a single adaptive process that learns, scales, and reduces exposure faster than ever.
Code to runtime coverage
From developer workflows to production environments, HackerOne provides end-to-end offensive security coverage. The result is complete visibility across the software development lifecycle and the live attack surface.
Leader in prioritization and validation
HackerOne maintains the deepest exploitability dataset in the industry, built from years of coordinated vulnerability disclosure, bug bounty findings, pentests, and real-world exploit intelligence. Every finding is grounded in evidence, providing clarity to prioritize action, direct resources efficiently, and accelerate risk reduction with confidence.