HackerOne Bug Bounty
Demo: See it in action
See the value of continuous security testing. HackerOne Bounty combines our SaaS platform with access to ethical hackers who find application defects that automated security tools miss.
Image
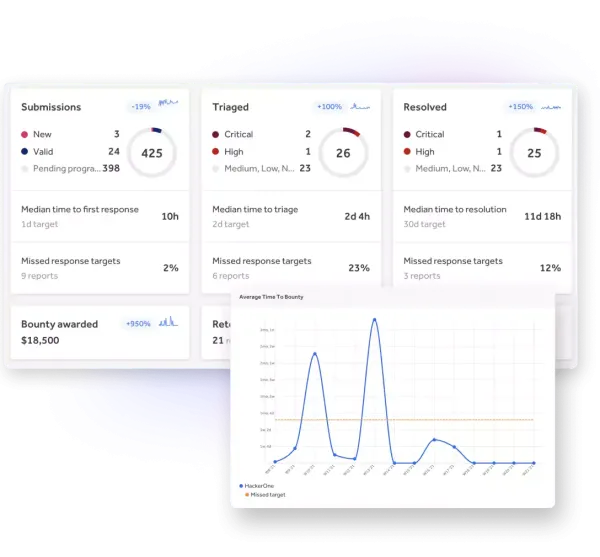
Security that adapts to your attack surface
HackerOne keeps tabs on your external assets, identifies hackers with the right skills, handles payments, triages, and prioritizes your vulnerabilities continuously to reduce risk across your evolving attack surface.
Find it and Fix it
Security experts find flaws before bad actors do.
Security experts find flaws before bad actors do.
Continuous observability
Eyes on your attack surface minimizes exploitability.
Eyes on your attack surface minimizes exploitability.
Rank the Risk
Prioritized findings drive fast remediation.
Prioritized findings drive fast remediation.