Information Security: Principles, Threats, and Solutions
What Is Information Security (InfoSec)?
20 Minute Read
Information Security (InfoSec) refers to the practice of protecting digital data, systems, and networks from unauthorized access, misuse, disclosure, disruption, modification, or destruction. It encompasses techniques, technologies, and strategies aimed at ensuring the confidentiality, integrity, and availability (CIA triad) of valuable information and systems.
InfoSec covers various aspects, including physical security, technical measures, and administrative controls to safeguard information assets from threats such as cyberattacks, data breaches, and natural disasters.
In this article:
- What Are the Principles of Information Security?
- Information Security vs. Cybersecurity
- 10 Common Information Security Threats and Attacks
- Types of Information Security
- What Is an Information Security Policy?
- Notable Information Security Solutions and Technologies
- What Is Information Security Risk Management?
- Information Security Best Practices
What Are the Principles of Information Security?
The CIA triad is a widely recognized model that forms the foundation of information security. These three principles are essential for ensuring the protection of sensitive data and the proper functioning of information systems.
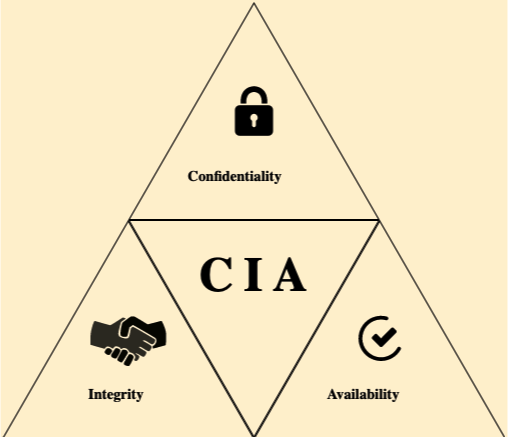
Confidentiality
This principle aims to protect sensitive information from unauthorized access and disclosure. Confidentiality ensures that only authorized users can access the information, while others are restricted. Techniques used to maintain confidentiality include encryption, password protection, user authentication, access controls, and the implementation of strict privacy policies.
Integrity
The integrity principle ensures that information remains accurate, complete, and consistent during its entire lifecycle. It prevents unauthorized users from modifying, tampering with, or deleting data. Integrity also ensures that authorized users can only make modifications in an approved manner. Measures for maintaining data integrity include checksums, digital signatures, version control, and strict access controls.
Availability
This principle ensures that information and systems are accessible to authorized users when needed. Availability is crucial for maintaining the functionality of information systems, minimizing downtime, and ensuring that authorized users can access the data they require. Strategies for maintaining availability include redundancy, backup systems, disaster recovery planning, robust infrastructure, and network load balancing.
Together, the CIA triad forms a comprehensive framework that helps organizations develop robust information security policies and procedures. It is essential for businesses to implement measures that address each aspect of the triad to safeguard their data and maintain the trust of stakeholders.
Information Security vs. Cybersecurity
Information security and cybersecurity are closely related fields that often overlap but have distinct focuses and scopes.
InfoSec deals with the protection of information in various forms, including digital, physical, and even verbal. It encompasses a wide range of measures, such as administrative, technical, and physical controls, to safeguard data from unauthorized access, disclosure, disruption, modification, or destruction. InfoSec addresses the security of data in storage, during processing, and in transit.
Cybersecurity, on the other hand, specifically focuses on protecting digital information, computer systems, networks, and electronic devices from cyber threats. This field is primarily concerned with defending against malicious attacks, such as hacking, malware, ransomware, and phishing, that originate from the internet or other digital channels. Cybersecurity covers various aspects, including network security, application security, endpoint security, and incident response.
While both information security and cybersecurity share common goals, such as maintaining the confidentiality, integrity, and availability of information, their scopes differ. InfoSec has a broader perspective that covers all forms of information, while cybersecurity is a more specialized domain that concentrates on digital assets. In practice, cybersecurity can be considered a subset of InfoSec that specifically addresses cyber threats and vulnerabilities.
10 Common Information Security Threats and Attacks
Information security threats and attacks are actions or events that can compromise the confidentiality, integrity, or availability of data and systems. They can originate from various sources, such as individuals, groups, or even natural events. Here are some common information security threats and attacks:
- Malware: Malicious software designed to infiltrate, damage, or disrupt systems. Malware includes viruses, worms, Trojans, ransomware, and spyware. It can steal sensitive information, cause system downtime, or provide unauthorized access to attackers.
- Phishing: A social engineering attack where attackers deceive users into revealing sensitive information or executing malicious actions, typically through fraudulent emails or messages that impersonate legitimate entities.
- Advanced persistent threats (APTs): Sophisticated, long-term cyberattacks, often state-sponsored, that target specific organizations or governments to steal sensitive information or cause disruption.
- Zero-day exploits: Attacks that exploit previously unknown vulnerabilities in software or hardware, giving developers no time to create patches or fixes.
- Insider threats: These involve employees, contractors, or partners with legitimate access to an organization's systems and data who misuse their privileges, either intentionally or unintentionally, to cause harm or compromise security.
- Password attacks: Attackers attempt to gain unauthorized access by cracking user passwords through methods such as brute force, dictionary attacks, or keylogging.
- Man-in-the-Middle (MitM) attacks: Attackers intercept communication between two parties, eavesdropping on, manipulating, or injecting malicious data into the conversation without the parties' knowledge.
- Distributed Denial of Service (DDoS): A coordinated attack on a target system or network by overwhelming it with a flood of traffic, rendering it inaccessible to legitimate users.
- Physical attacks: Unauthorized access, theft, or damage to physical assets, such as computer systems, servers, or storage devices, which can lead to data loss or disruption of operations.
- Natural disasters: Events like floods, earthquakes, or fires that can cause physical damage to infrastructure, leading to data loss or system downtime.
Types of Information Security
Here are common types of information security in modern organizations:
Network security
This type of security encompasses the protection of computer networks against unauthorized access or misuse. Network security involves a range of technologies, such as firewalls, intrusion detection/prevention systems, virtual private networks (VPNs), and secure protocols, to ensure data confidentiality, integrity, and availability.
Application security
Application security involves securing software applications from cyber threats, such as malware, SQL injection attacks, and cross-site scripting (XSS). Application security solutions include secure coding practices, penetration testing, and vulnerability assessments.
Data security
Data security is the practice of protecting sensitive data from unauthorized access, use, disclosure, or destruction. Data security involves a range of technologies, such as encryption, access control, and backup and restore procedures, to ensure data confidentiality, integrity, and availability.
Endpoint security
Endpoint security focuses on protecting endpoints, such as laptops, desktops, servers, and mobile devices, from cyber threats. Traditional endpoint security technologies include antivirus and anti-malware software and firewalls. Modern endpoint security includes advanced solutions like endpoint detection and response (EDR) that can protect against zero-day threats.
Mobile security
Mobile security refers to the protection of mobile devices, applications, and data from unauthorized access or exploitation. Mobile security solutions include mobile device management (MDM) software, secure mobile application development, and secure communication protocols.
Cloud security
Cloud security involves the protection of cloud-based data, applications, and infrastructure. It covers a variety of security concerns, including data privacy, access control, threat management, and compliance.
IoT security
IoT security involves securing the networks, devices, and data associated with the Internet of Things (IoT). IoT security covers a range of security issues, including data privacy, access control, device authentication, and network security.
What Is an Information Security Policy?
An information security policy is a formal, documented set of rules and guidelines that an organization establishes to protect its information assets and ensure the confidentiality, integrity, and availability of its data.
This policy serves as a framework for managing risk, defining acceptable behaviors, and setting security expectations for employees, contractors, partners, and other stakeholders. It also helps organizations comply with legal, regulatory, and industry requirements.
An effective information security policy typically includes the following components:
- Purpose: A clear statement outlining the policy's objectives and the organization's commitment to information security.
- Scope: A description of the systems, data, and personnel covered by the policy, including any third-party vendors or partners.
- Roles and responsibilities: A definition of the roles and responsibilities of various stakeholders, such as management, IT staff, and employees, in implementing, maintaining, and enforcing the policy.
- Asset management: Guidelines for identifying, classifying, and managing the organization's information assets to ensure appropriate protection levels.
- Access control: Rules for granting and revoking access to systems and data, including user authentication, authorization, and password management.
- Incident response: Procedures for detecting, reporting, and responding to security incidents, including communication protocols and escalation paths.
- Physical security: Measures to protect the organization's facilities, equipment, and information assets from unauthorized access, theft, or damage.
- Training and awareness: Requirements for regular employee training and awareness programs to promote a culture of security and ensure that personnel understand their responsibilities.
- Monitoring and auditing: Processes for monitoring compliance with the policy, including regular audits, assessments, and reviews to identify gaps and areas for improvement.
- Policy review and updates: A schedule for periodically reviewing and updating the policy to ensure it remains relevant, effective, and aligned with the organization's evolving needs and the changing threat landscape.
An information security policy is a critical component of an organization's overall security strategy, as it provides a foundation for implementing technical measures, administrative controls, and best practices to safeguard its information assets.
Notable Information Security Solutions and Technologies
It is not possible to list the thousands of security tools and technologies used by modern security organizations. However, here are some of the most common tools that are typically present in a mature security stack.
Firewalls
A firewall is a network security device that monitors incoming and outgoing traffic, acting as a barrier between a trusted internal network and untrusted external networks. Firewalls use predefined rules to allow or block traffic based on factors like IP addresses, ports, and protocols, preventing unauthorized access and malicious traffic from entering the network.
Intrusion Detection System (IDS) and Intrusion Prevention System (IPS)
IDS is a security technology that monitors network traffic for signs of malicious activity or policy violations. If detected, it generates alerts for security personnel to investigate. IPS, on the other hand, is an active system that not only detects but also blocks or prevents malicious traffic in real-time. Both IDS and IPS can be host-based (focusing on a single system) or network-based (monitoring the entire network).
Security Incident and Event Management (SIEM)
SIEM solutions collect, aggregate, and analyze log data from various sources, such as firewalls, IDS/IPS, servers, and applications. They help organizations detect, investigate, and respond to security incidents by providing real-time monitoring, advanced analytics, and automated response capabilities. SIEM solutions also enable compliance with regulatory requirements through centralized reporting and auditing.
Vulnerability Management
Vulnerability Management is the process of identifying, evaluating, and addressing security weaknesses in an organization's IT infrastructure, software, and applications. This process involves continuous scanning, monitoring, and assessment of systems to detect possible vulnerabilities.
Once vulnerabilities are identified, organizations prioritize and remediate them through patching, configuration changes, or other security controls. The main goal of vulnerability management is to reduce the likelihood and impact of successful cyberattacks by minimizing exploitable vulnerabilities in the environment.
Attack Surface Management
Attack surface management is the practice of identifying, mapping, and reducing the potential entry points (attack vectors) an adversary could use to compromise an organization's IT systems and data. This involves understanding and securing all components of the IT environment, including hardware, software, networks, cloud services, and third-party integrations.
By minimizing the attack surface, organizations can reduce the risk of cyberattacks, lower the chances of successful breaches, and improve their overall security posture. Attack surface management includes activities such as continuous monitoring, threat modeling, secure configuration management, and proper access control implementation.
Cloud Security Posture Management (CSPM)
CSPM solutions help organizations maintain and improve their security posture in cloud environments by continuously monitoring cloud infrastructure, identifying misconfigurations, and providing recommendations for remediation. CSPM tools enable organizations to enforce security policies, assess compliance, and mitigate risks associated with cloud adoption.
Threat Intelligence
Threat intelligence refers to the collection, analysis, and sharing of information about existing and emerging threats, such as threat actors, tactics, techniques, and procedures (TTPs), vulnerabilities, and indicators of compromise (IoCs). Threat intelligence solutions help organizations proactively identify and mitigate risks, prioritize security efforts, and improve their overall security posture.
What Is Information Security Risk Management?
Information Security Risk Management is the process of identifying, assessing, prioritizing, and mitigating risks associated with an organization's information assets and IT infrastructure. The goal of information security risk management is to protect the confidentiality, integrity, and availability of information assets while minimizing the impact of security incidents on the organization's operations, reputation, and legal obligations.
The process typically involves the following steps:
- Identify assets: Create an inventory of information assets, such as hardware, software, data, and network components, and determine their value to the organization.
- Identify threats and vulnerabilities: Analyze the potential threats and vulnerabilities that could compromise the security of the information assets. Threats can come from various sources, such as hackers, malware, natural disasters, or human error. Vulnerabilities refer to weaknesses in systems, processes, or policies that could be exploited by threats.
- Assess risks: Evaluate the likelihood and potential impact of identified threats and vulnerabilities on the information assets. This can be done using qualitative or quantitative methods, such as risk matrices, scoring systems, or probabilistic models.
- Prioritize risks: Rank the identified risks based on their potential impact and likelihood, focusing on the most significant risks that require immediate attention and resources.
- Develop mitigation strategies: Design and implement security controls, policies, and procedures to mitigate the prioritized risks. These may include preventive measures (e.g., firewalls, encryption), detective measures (e.g., intrusion detection systems, log monitoring), and corrective measures (e.g., incident response plans, backups).
- Monitor and review: Continuously monitor the effectiveness of the implemented security controls and review the risk management process to ensure that it remains relevant and up-to-date. This involves staying informed about emerging threats and vulnerabilities, as well as changes in the organization's assets, operations, and legal requirements.
- Report and communicate: Regularly report on the status of information security risks and mitigation efforts to stakeholders, such as senior management, board members, and auditors. Clear communication helps ensure that everyone in the organization understands their roles and responsibilities in maintaining information security.
Information Security Best Practices
Develop an Incident Response Plan
An incident response plan prepares an organization to effectively manage and respond to security incidents, minimizing the potential impact and ensuring a swift return to normal operations.
By establishing clear roles and responsibilities, outlining response procedures, and promoting continuous improvement, an incident response plan helps organizations maintain a strong security posture and protect their critical assets.
Adopt DevSecOps
DevSecOps, which stands for Development, Security, and Operations, integrates security practices throughout the software development lifecycle. By incorporating security as an integral part of the development process, DevSecOps aims to reduce vulnerabilities, ensure faster response to security incidents, and promote a culture of shared responsibility for security across the entire organization.
Create a Red Team and Blue Team
Red team-blue team exercises involve two groups working together to strengthen an organization's security posture. The red team simulates real-world attacks, while the blue team defends against these attacks, detects intrusions, and mitigates threats.
By engaging in these exercises, organizations can strengthen their security posture, improve incident response capabilities, and foster a culture of shared responsibility for security.
Conduct Penetration Testing
Penetration testing involves simulating real-world cyberattacks on an organization's systems, networks, or applications to identify vulnerabilities and evaluate their security defenses. By conducting regular penetration tests, organizations can discover weaknesses in their security controls, assess their resilience against attacks, and remediate issues before they are exploited.
Automate Vulnerability Management
Implementing automated vulnerability management tools, such as vulnerability scanners and patch management systems, helps organizations regularly identify, assess, prioritize, and remediate security vulnerabilities in their systems. This continuous process reduces the window of opportunity for attackers to exploit known weaknesses and improves the organization's overall security posture.
Implement Data Encryption
Data encryption protects sensitive data from unauthorized access and ensures the confidentiality and integrity of that data, both in transit and at rest.
By implementing strong encryption measures, organizations can minimize the risk of data breaches, build trust with stakeholders, and maintain a robust security posture.
Leverage Strong Authentication
Implementing strong authentication mechanisms, such as multi-factor authentication (MFA), helps ensure that only authorized users can access sensitive data and systems. MFA combines multiple methods of verification, such as something the user knows (password), something the user has (security token or smartphone), or something the user is (biometrics). This layered approach significantly reduces the risk of unauthorized access due to compromised credentials.
Educate and Train Users
Human error is often a significant factor in information security breaches. Providing regular security awareness training to employees, contractors, and partners helps build a security-conscious culture and ensures that users understand their responsibilities in protecting the organization's data. Topics covered in such training may include phishing awareness, safe password practices, and how to report suspected security incidents.
Information Security with HackerOne
The HackerOne Attack Resistance Platform is an essential component of Information Security strategies. With a portfolio of preemptive application security products combined with the largest community of skilled security experts, organizations add a continual layer of protection to their growing attack surface to ensure their information is safe.