Introducing HackerOne Assets

Understanding where the critical flaws lie within your organization's attack surface is critical—but complicated. After all, your attack surface includes your infrastructure, network, software, applications, devices, and the extended supply chain. But it doesn’t stop there. Digital transformation, cloud adoption, the shift to remote work, mergers and acquisitions (M&A), and shadow IT further muddy the waters for today’s security leaders.
This blog post is part 1 of an ongoing series that provide deep dives into HackerOne Assets and its core capabilities.
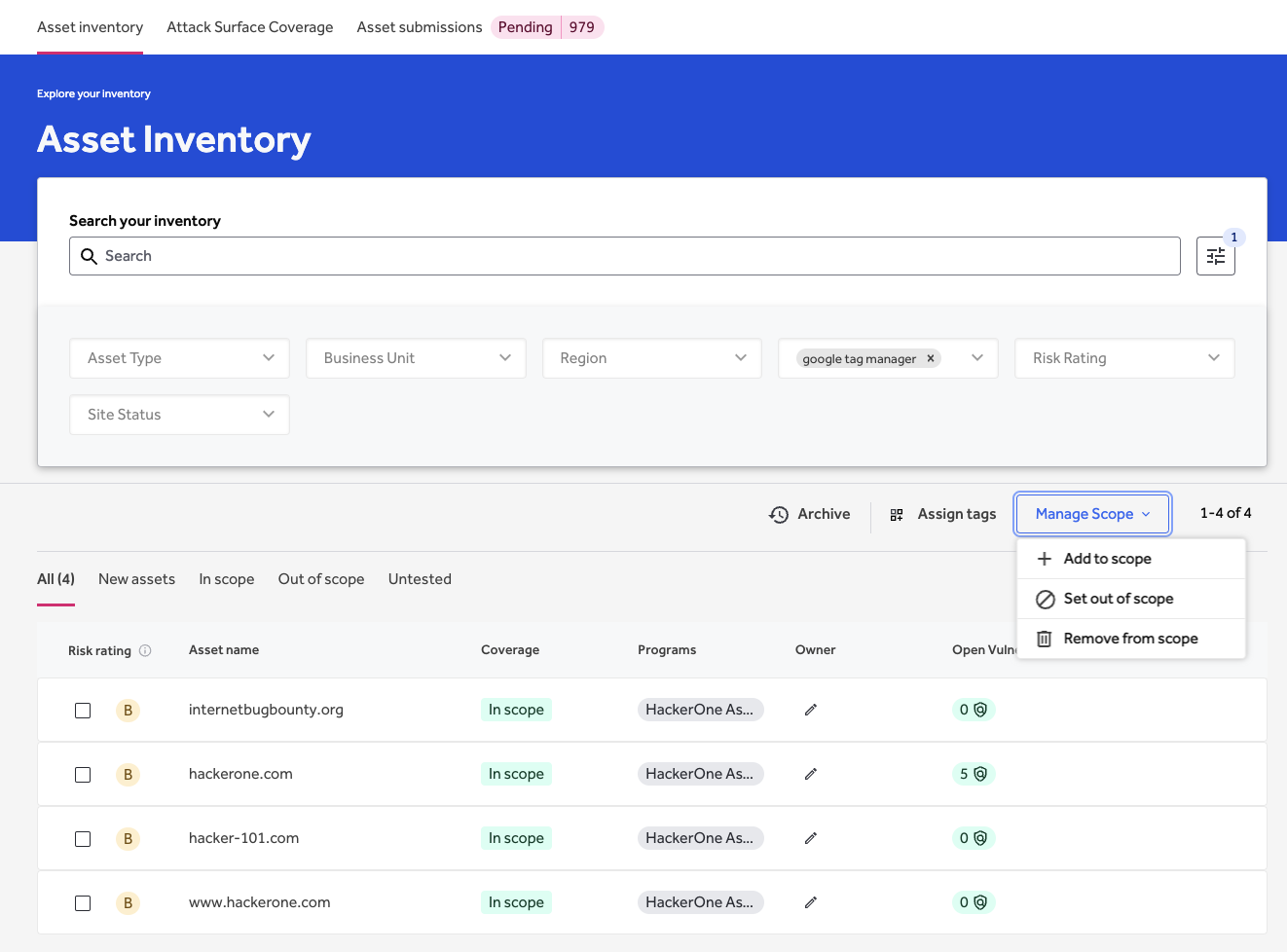
Having the right automated tools to monitor your known attack surface is crucial in managing risk, but what about the vulnerabilities in unmanaged or unknown assets? Achieving visibility across your expanding digital footprint and associated weaknesses requires going beyond automation. That's where HackerOne Assets comes in (Figure 1).
What is HackerOne Assets?
HackerOne Assets is the newest addition to our evolving Attack Resistance Management Platform. It combines the core capabilities of Attack Surface Management (ASM) with the reconnaissance skills of ethical hackers to bring visibility, tracking, and risk propensity to an organization's digital asset landscape.
How It Works
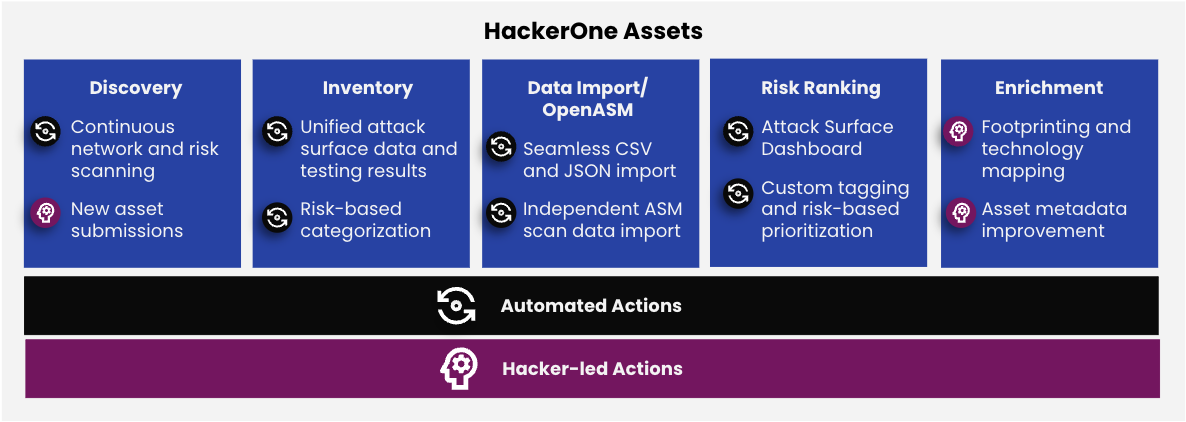
HackerOne uses a hybrid approach that blends automation and hacker intelligence to deliver comprehensive knowledge to organizations, all within our Attack Resistance Management platform (Figure 2).
- Automated Actions help customers discover and risk-rank internet-facing assets continuously and funnel the collected scan data into our unified security platform.
- Hacker-led Actions facilitate human security analysis and testing, ensuring that known and unknown assets are periodically assessed for risk and mapped according to their characteristics (e.g. region, risk, technology stack, or PII).
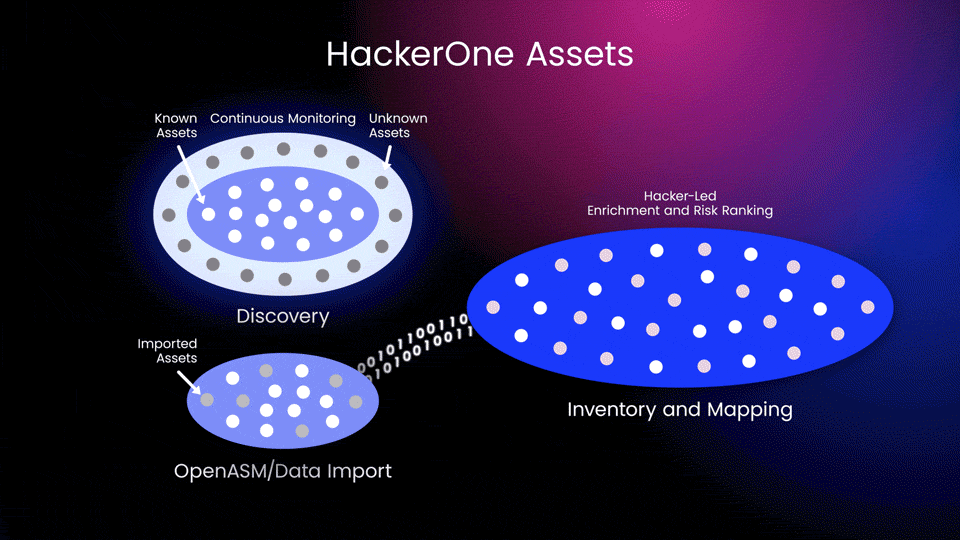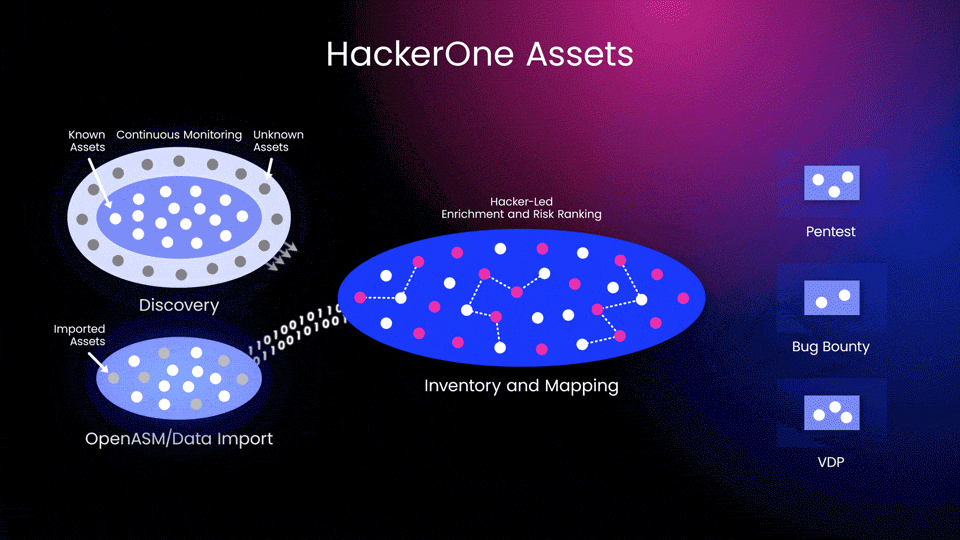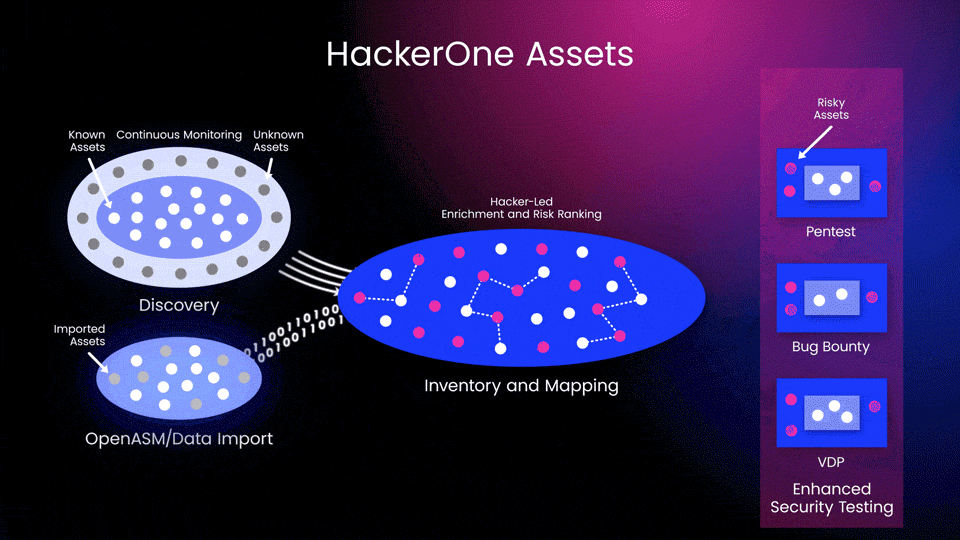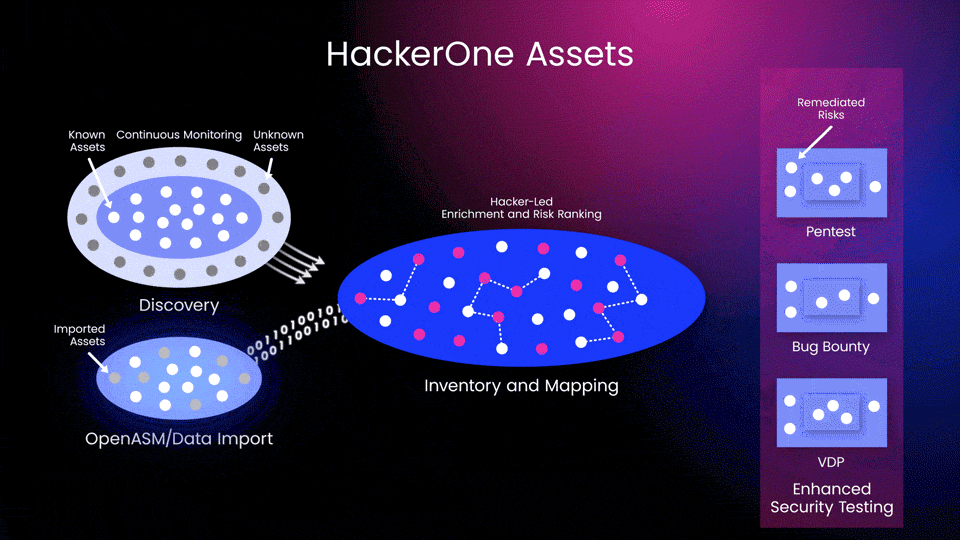
Teams can then use the validated risk and asset knowledge based on ASM scan data to prioritize security actions. This insight helps them amplify the effectiveness of testing scopes for vulnerability disclosure programs, bug bounties, and pentest engagements for continual protection and remediation (Figure 3).
What’s on the Horizon?
Early collaboration with our customers enabled us to gain insight into ASM imperatives and validate our unique approach to reducing attack surface risk. The combination of our unified, automated asset security and our skilled community of ethical hackers delivers the ASM force multiplier you need to keep your organization safe.
With the introduction of HackerOne Assets, we have enabled powerful new security capabilities in our Attack Resistance Management platform, including:
- OpenASM and Assets API
- Asset inventory (Figure 1)
- Automated and hacker-led asset discovery
- Continuous scanning and monitoring
- Risk ranking
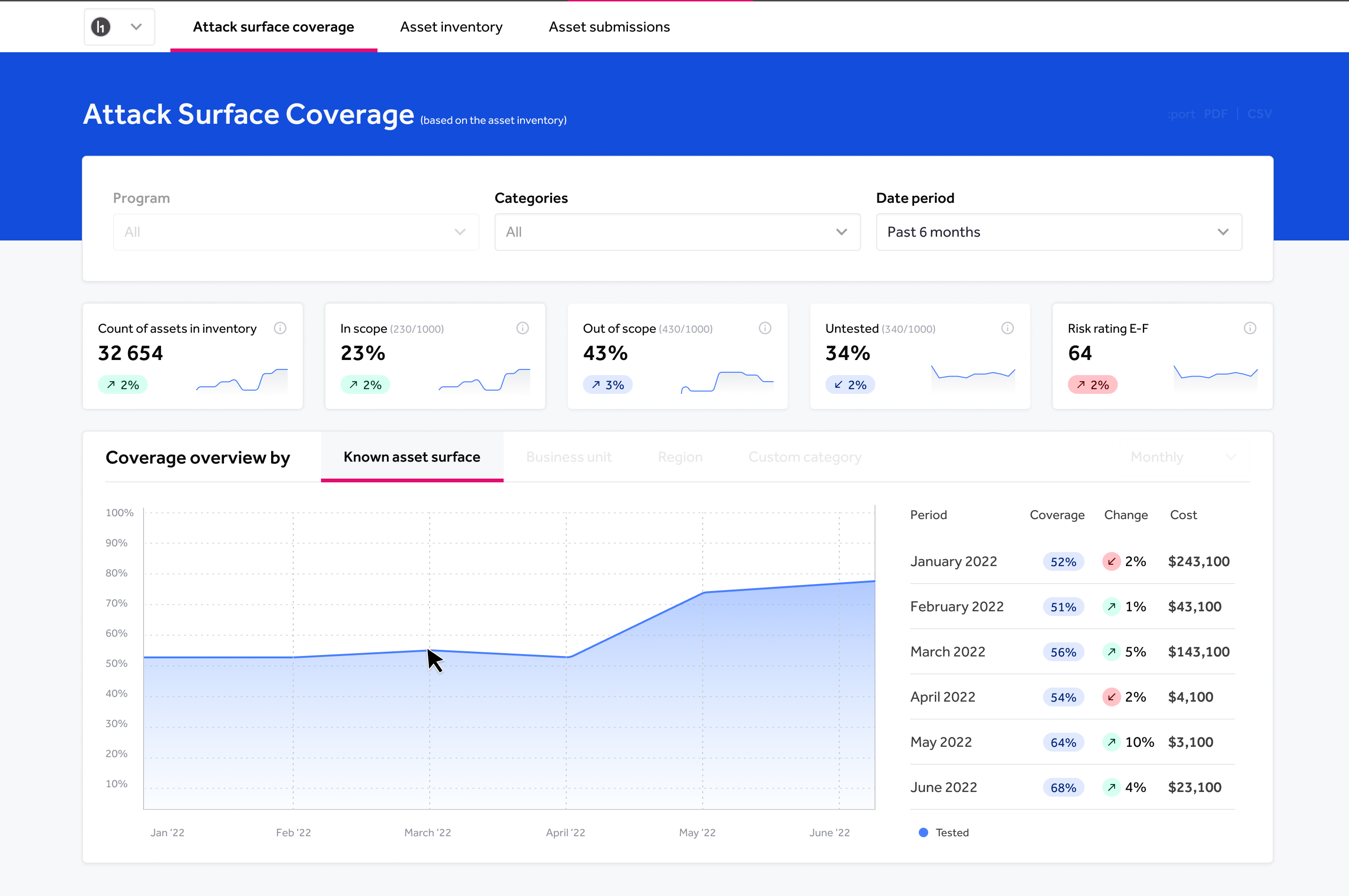
- Attack surface coverage (Figure 4)
We’ll be adding new capabilities to HackerOne Assets to extend the effectiveness of your Attack Resistance Management strategy. Stay tuned for more product news and updates!
Curious to know more? Get in touch with our security experts to explore the outcomes of Attack Resistance Management.
The Ultimate Guide to Managing Ethical and Security Risks in AI