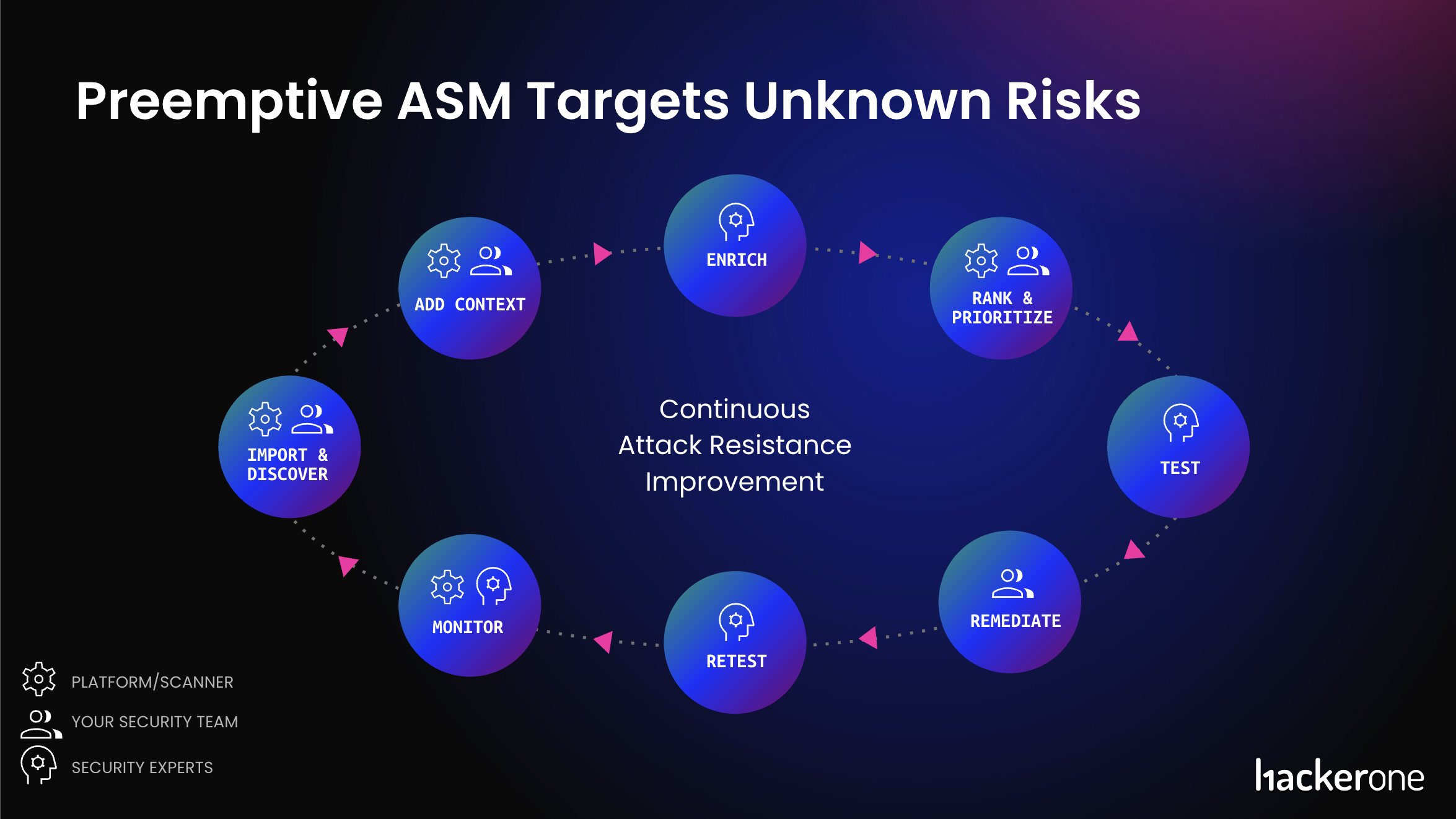
1. Discover and Import
Maintaining an up-to-date inventory of all your internet-facing assets is crucial for effective risk management. HackerOne automates continuous attack surface discovery, mapping your organization's external perimeter using your brand name. This approach uncovers previously unknown and unmanaged application risks, checks for misconfigurations, and detects outdated software.
While automation is valuable, human intuition is indispensable for achieving the most impactful results. HackerOne's platform workflows harness the expertise of ethical hackers, identifying rogue assets that may elude automated tools and streamlining your security process. Your team can effectively discover and address unknown risks by uniting human expertise with automation.
Teams can also import asset data from scan results and other ASM solutions to comprehensively view and manage their organization's attack surface. All assets—uncovered through automation and human intelligence—appear in the platform, creating a single source of truth for your organization.
2. Add Context
Deduplicating incoming asset data and adding metadata, such as asset ownership and system configuration, allows you to better understand each asset. This valuable context helps you make informed decisions about security priorities and streamlines your security testing process. Additionally, fully customizable, in-platform taxonomy capability enables security and engineering teams to set up the tags to fit how they work without being limited by a system.
3. Enrich
HackerOne's automated and human-led enrichment capabilities provide a more accurate picture of an organization's external assets. The automated enrichment outputs improve an asset's metadata by adding new information or correcting the existing information regarding the underlying technologies, geolocation, and observed risks. Examples of risk might include vulnerable software, misconfigurations, open ports, and information leaks.
On top of the automated enrichment, ethical hackers are crucial in further enriching your assets by submitting additional context. These activities lead to understanding any asset landscape better by figuring out essential information such as the underlying technology stack, cloud providers, and which assets contain PII or have login pages with the collective insights of security experts.
The enriched asset data helps paint a more accurate picture of your organization's risk landscape and informs subsequent adversarial testing performance.
4. Risk Rank and Prioritize
A top-tier ASM program should efficiently detect vulnerable, misconfigured, or outdated software in your internet-facing assets by analyzing their technology stack and host header information. When it identifies outdated software with publicly known Common Vulnerabilities and Exposures (CVE), the program calculates a risk score based on the Common Vulnerability Scoring System (CVSS) Score. HackerOne platform enhances this information by providing context for each identified CVE, including a vulnerability description, metadata like Common Weakness Enumeration (CWE) classification, and the CVSS score.
Assets should receive a risk rating from A to F, with A representing the lowest risk and F the highest. This rating considers potential impact, the likelihood of exploitation, and existing security controls. Moreover, the HackerOne platform displays the real-world exploitability of each CVE based on platform data derived from tens of thousands of reports across thousands of security-conscious organizations. This context helps your team prioritize vulnerability fixes.
The combined insights from the risk rating methodology and in-platform CVE Intelligence enable security teams to effectively track and prioritize high-risk assets for remediation.
5. Test
Typically, a security team might accept a new asset and complete basic remediations, then add the asset to an active bug bounty, Vulnerability Disclosure Program (VDP), or a pentesting engagement. This process ensures that newly identified risks are fed into established risk reduction processes instead of slipping through the cracks.
Learn what human security testing can provide to your business.
6. Remediate and Retest
Identifying vulnerabilities is only the first step; addressing them is equally crucial. Highlight asset risk severity and provide actionable remediation steps. Platform integrations with leading ticketing systems, SIEM, and SOAR solutions support function-specific remediation workflows while retesting ensures the effectiveness of implemented security controls.
As vulnerability reports come in and teams deploy fixes, external validation is crucial to address vulnerabilities effectively. Retesting allows security researchers to verify whether a fix has been implemented and your assets' data is secured. HackerOne's native retesting feature makes it easy for organizations to select pentesters or ethical hackers, depending on their security testing program, and seamlessly verify fixes.
7. Monitor
Ongoing monitoring of your digital estate through continuous discovery workflows and human-led discovery is essential for identifying new assets and risks. The platform analytics offer powerful insights and actionable guidance based on asset risk and coverage trends, enabling you to track progress and make adequate security decisions.
Closed-Loop Attack Resistance Powered by HackerOne
This comprehensive lifecycle streamlines your digital asset inventory for adversarial testing and attack surface management by providing a single source of truth. Unified vulnerability reports and risk-ranked asset data enhance the effectiveness of a Vulnerability Disclosure Program, bug bounty, and pentest engagements, ensuring continuous protection and remediation.
The closed-loop process enables security teams to maintain a 1-1 correlation between their real-time attack surface and risk-based vulnerability mitigation. By adopting the complete HackerOne Platform, organizations can effectively control their attack surface from all angles and boost their ability to resist attacks.
Ready to learn more? Contact us to increase your team’s ability to protect your attack surface and act on what matters most!






















