Today, HackerOne is thrilled to release Custom Fields, the latest way to sharpen security workflows and software development cycles. Custom Fields empowers teams to gain new insights into data by adding details such as ownership, risk category and root cause to vulnerability reports.
Why it matters
The global average cost of a data breach is $3.86 million, up 6.4 percent year over year, according to IBM. With the vast troves of confidential information being loaded, altered and analyzed with every update and new line of code, it’s more important than ever for companies to go beyond the call of duty when it comes to locating and patching vulnerabilities. Not only should they be able to identify the various security holes created along the way, but also understand which teams and technologies have more threat risk, better prioritize how to prevent and respond to actual risks, and diagnose any trends.
How it works
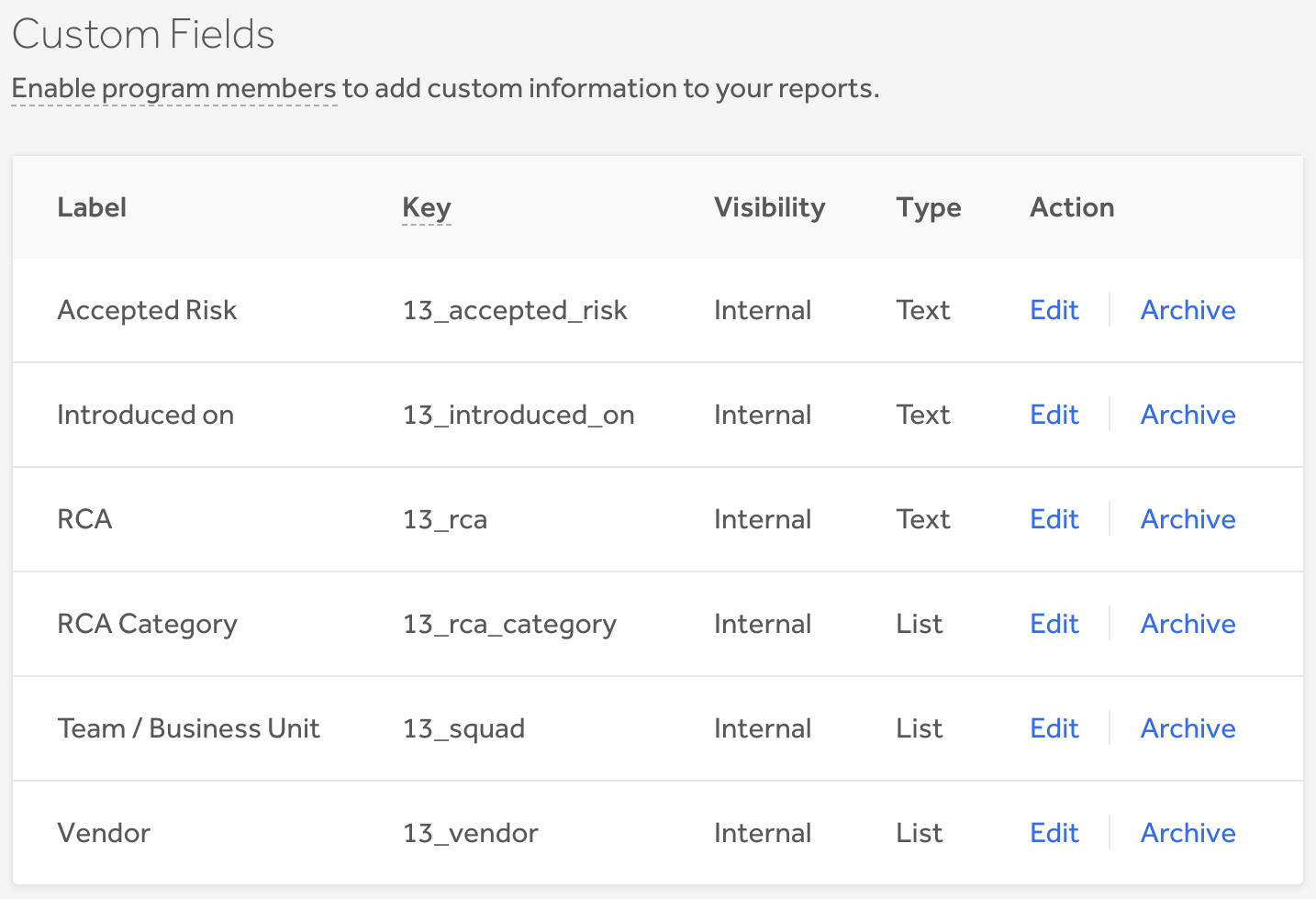
Enter Custom Fields, a proprietary system built to align reports with internal stakeholders. Custom Fields improves internal, cross-functional communication by tagging specific business units, application versions, regions, sub-brands, or teams. At HackerOne, we're using custom fields to track the engineering team associated with each report. Labels can be easily added and corresponding values can be entered through a pre-configured list of items or through open-ended text. The feature can be easily configured into existing program settings by program administrators.
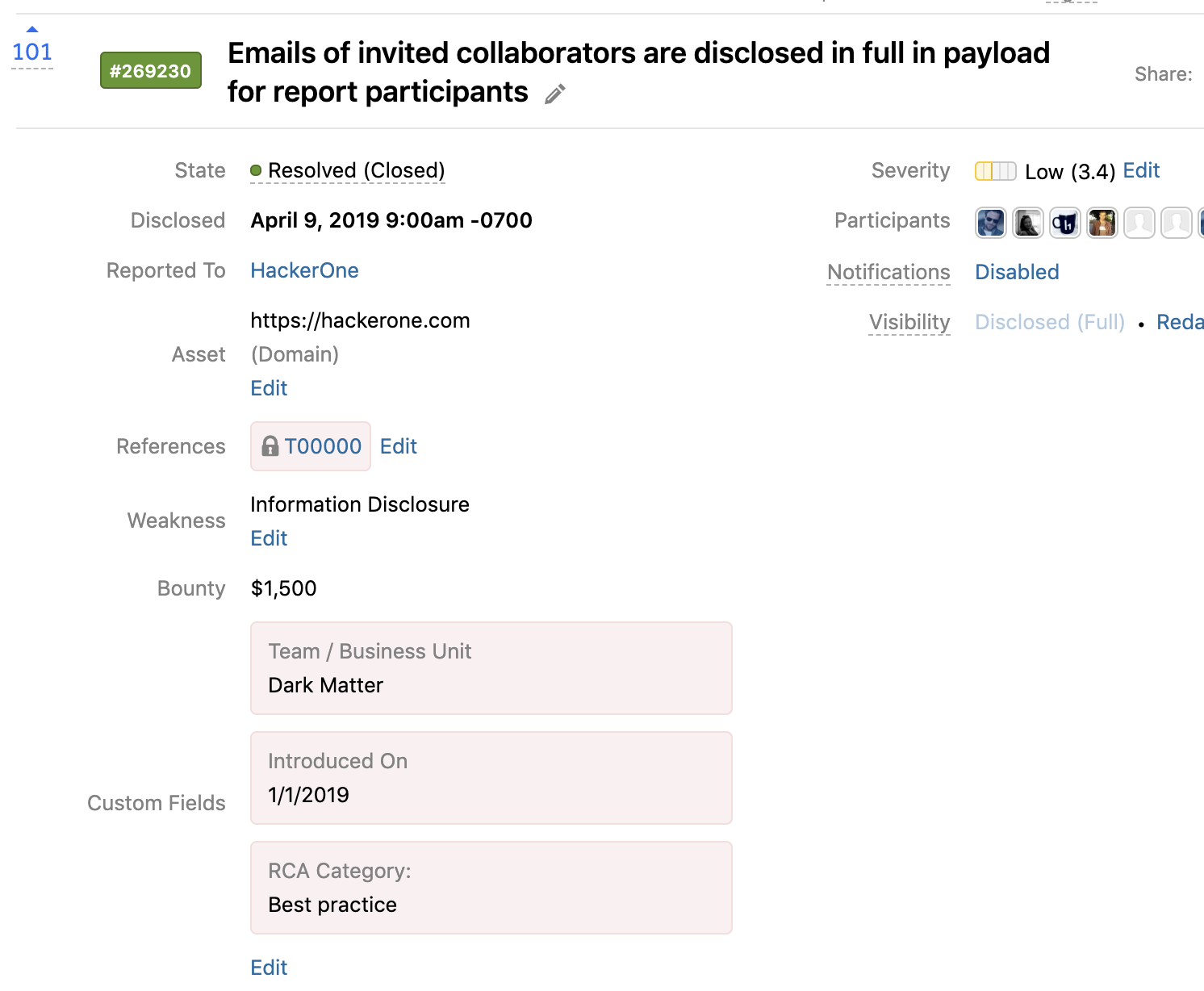
With each new report received, customers can set the fields directly into the report metadata section.
Workflow Customization
Defining a workflow that works for your team is vital to your bottom line and can relieve chaos and confusion for both short-term and ongoing projects. Custom Fields helps create order for security teams by mapping data across third-party issue trackers like Jira and the HackerOne API and filtering the HackerOne inbox based on its values.
To begin to customize your workflow with Custom Fields, set up Inbox filters that correspond with Custom Fields tags and categories through inbox views. By using a combination of values, customers see more dynamic and relevant slices of their reports.
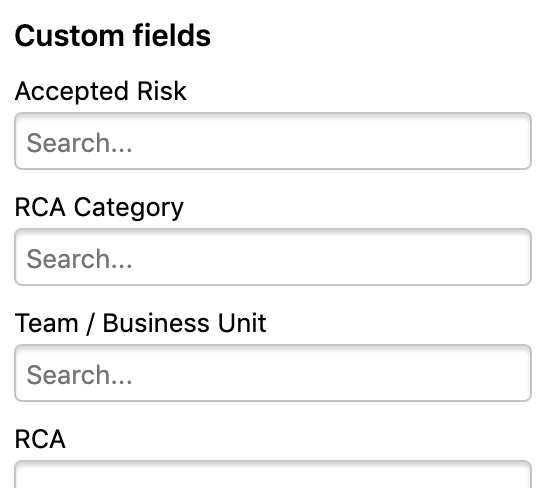
Custom Fields can also be used to escalate tasks to third-party issue trackers like Jira. Values are then referenceable when configuring integrations and will be automatically added to the corresponding ticket or issue in the system.
Data Analysis and Beyond
By leveraging Custom Fields, companies unlock new insights to fuel workflows and add value to reports. To analyze this data in the methods that work best for teams, Custom Field values can be exported with report data via both CSV and API.
As the most requested feature from HackerOne customers to date, the opportunities to implement Custom Fields are endless, and the customers who participated in its Beta launch are already seeing immense value from the insights. Just a handful of the many ways customers are already leveraging this new feature include:
- Specifying ownership for a particular vulnerability for analysis or charge back purposes by noting one team member or business unit as responsible for the report
- Root cause analysis documentation to power investigation of common causes and trends in vulnerabilities found throughout product life cycles
- Streamlining tracking by recording an internal vulnerability ID to implement across systems
- Setting a custom CWE or weakness classification to help identify, fix, and prevent future security flaws
The Custom Field feature is available immediately to our Enterprise customers. You can read more about the feature in our product documentation and API documentation for more information and detailed how-tos.
We’re always looking to improve our platform. Keep an eye on our blog, and please let us know if you have feedback or suggestions.






















